DBMSs abd Web Security
Internet communication relies on TCP/IP the underlying protocol
However, TCP/IP and HTTP were bot designed with security in mind
Without special software, all Internet traffic travels 'in the clear' and anyone who monitors traffic can read it.
The challenge is to transmit and receive information over the Internet while ensuring that:
Measures include:
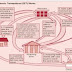
A SET Transaction
However, TCP/IP and HTTP were bot designed with security in mind
Without special software, all Internet traffic travels 'in the clear' and anyone who monitors traffic can read it.
The challenge is to transmit and receive information over the Internet while ensuring that:
- It is inaccessibly to anyone but the sender and receiver (privacy)
- It has not been changed during transmission (integrity)
- The receiver can be sure it came from the sender (authenticity)
- The sender can be sure the receiver is genuine (non-fabrication)
- The sender cannot deny he or she sent it (non-repudiation)
Measures include:
- Proxy servers
- Firewalls
- Message digest algorithms and digital signatures
- Digital certificates
- Kerberos
- Secure sockets layer (SSL) and Secure HTTP (SHTTP)
- Secure Electronic Transactions (SET) and Secure Transaction Technology (SST)
- Java Security
- ActiveX Security
A SET Transaction









No comments