Question Paper
1. Which of the following options is the closest in meaning to the phrase underlined in the
sentence below?
It is fascinating to see life forms cope with varied environmental conditions.
(A) Adopt to (B) Adapt to (C) Adept in (D) Accept with
Answer: (B)
2. Choose the most appropriate word from the options given below to complete the following
sentence.
He could not understand the judges awarding her the first prize, because he thought that her
performance was quite ___________________.
(A) Superb (B) Medium (C) Mediocre (D) Exhilarating
Answer: (C)
3. In a press meet on the recent scam, the minister said, “The buck stops here”. What did the
minister convey by the statement?
(A) He wants all the money (B) He will return the money
(C) He will assume final responsibility (D) He will resist all enquiries
Answer: (C)
4. If ( ) ( )
2 2 2 z 1/ z 98, compute z 1/ z + = +
Answer: (96)
Exp: Expanding
2 2
2 2
1 1 1 z 2.z. 98 z 96
z z z
+ + = ⇒ + =
5. The roots of 2
ax bx c 0 + + = are real and positive a, b and c are real. Then 2
ax b x c 0 + + =
has
(A) No roots (B) 2 real roots (C) 3 real roots (D) 4 real roots
Answer: (D)
Exp: ax2
+bx+c=0
for roots to be real & +ve
b2
-4ac>0
This will have 2 real positive roots.
2
ax b x c 0 + + =
This can be written as;
2
2
ax bx c
Discri min ant b 4ac 0
+ +
= − >
2
2
2
ax bx c
( b) 4ac
b 4ac
− +
− −
⇒ −
Is also >0. This will have real roots
⇒ This will have 4 real roots.
CS-GATE-2014 PAPER-01| www.gateforum.com
India’s No.1 institute for GATE Training 1 Lakh+ Students trained till date 65+ Centers across India
2
Q.No. 6 – 10 Carry One Mark Each
6. The Palghat Gap (or Palakkad Gap), a region about 30 km wide in the southern part of the
Western Ghats in India, is lower than the hilly terrain to its north and south. The exact
reasons for the formation of this gap are not clear. It results in the neighbouring regions of
Tamil Nadu getting more rainfall from the South West monsoon and the neighbouring
regions of Kerala having higher summer temperatures.
What can be inferred from this passage?
(A) The Palghat gap is caused by high rainfall and high temperatures in southern Tamil Nadu
and Kerala
(B) The regions in Tamil Nadu and Kerala that are near the Palghat Gap are low–lying
(C) The low terrain of the Palghat Gap has a significant impact on weather patterns in
neighbouring parts of Tamil Nadu and Kerala
(D) Higher summer temperatures result in higher rainfall near the Palghat Gap area
Answer: (C)
7. Geneticists say that they are very close to confirming the genetic roots of psychiatric illnesses
such as depression and schizophrenia, and consequently, that doctors will be able to eradicate
these diseases through early identification and gene therapy.
On which of the following assumptions does the statement above rely?
(A) Strategies are now available for eliminating psychiatric illnesses
(B) Certain psychiatric illnesses have a genetic basis
(C) All human diseases can be traced back to genes and how they are expressed
(D) In the future, genetics will become the only relevant field for identifying psychiatric
illnesses
Answer: (B)
8. Round–trip tickets to a tourist destination are eligible for a discount of 10% on the total fare.
In addition, groups of 4 or more get a discount of 5% on the total fare. If the one way single
person fare is Rs 100, a group of 5 tourists purchasing round–trip tickets will be charged Rs
___________
Answer: (850)
Exp: One way force =100
Two way fare per person=200
5 persons=1000/-
Total discount applicable=10+5=15%
15 Discount amount 1000 150
100
= × =
Amount to be paid=1000-150=850
9. In a survey, 300 respondents were asked whether they own a vehicle or not. If yes, they were
further asked to mention whether they own a car or scooter or both. Their responses are
tabulated below. What percent of respondents do not own a scooter?
Men Women
Own vehicle
Car 40 34
Scooter 30 20
Both 60 46
Do not own vehicle 20 50
Answer: (48)
Exp: Total respondents=300
Those who don’t have scooter
⇒ Men= 40+20=60
84 Women 34 50
144
144 % 100 48%
300
= + =
= × =
10. When a point inside of a tetrahedron (a solid with four triangular surfaces) is connected by
straight lines to its corners, how many (new) internal planes are created with these lines?
_______________________
Answer: (6)
4
Q. No. 1 – 25 Carry One Mark Each
1. Consider the statement:
“Not all that glitters is gold”
Predicate glitters (x) is true if x glitters and predicate gold (x) is true if x is gold. Which one
of the following logical formulae represents the above statement?
(A) ∀x; glitters x gold x ( ) ⇒¬ ( ) (B) ∀x; gold x glitters x ( ) ⇒ ( )
(C) ∃ ∧ ¬ x; gold x glitters x ( ) ( ) (D) ∃ ∧ ¬ x; glitters x gold x ( ) ( )
Answer: (D)
Exp: It means “It is false that every glitter is gold” or “some glitters are not gold”.
Then we can say “atleast one glitter object is not gold”.
2. Suppose you break a stick of unit length at a point chosen uniformly at random. Then the
expected length of the shorter stick is ________ .
Answer: (0.25)
Exp: The smaller sticks, therefore, will range in length from almost 0 meters up to a maximum of
0.5 meters, with each length equally possible.
Thus, the average length will be about 0.25 meters, or about a quarter of the stick.
3. Let G=(V,E) be a directed graph where V is the set of vertices and E the set of edges. Then
which one of the following graphs has the same strongly connected components as G?
(A G V,E where E u,v | u,v E ) 1 1 1 = = ∉ ( ) {( ) ( ) }
(B G V,E where E u,v | v,u E ) 2 2 2 = = ∉ ( ) {( ) ( ) }
(C G V,E where E u,v | there is a path of length 2 from ) 3 3 3 = = ≤ ( ) {( ) u to v in E}
(D G V ,E where V is the set of vertices in G which are ) 4 4 4 = ( ) not isolated
Answer: (B)
Exp: Take an example for Graph G
. .
A B
Then option A and D will be eliminated.
Let G is below graph
Then G3 is a graph with below structure
In G the numbers of strongly connected components are 2 where as in G3 it is only one.
A B
A B
4 Consider the following system of equations:
3x 2y 1
4x 7z 1
x y z 3
x 2y 7z 0
+ =
+ =
+ + =
− + =
The number of solutions for this system is __________________
Answer: (1)
Exp: 3x 2y 1
4x 7z 1
x y z 3
x 2y 7z 0
+ =
+ =
+ + =
− + =
Augmented matrix is
3 2 0 1
4 0 7 1
1 1 1 3
1 2 7 0
−
1 3
1 1 1 3
4 0 7 1
R R
3 2 0 1
1 2 7 0
↔
−
2 2 1 3 3 1 4 4 1
3 3 2
4 4 2
4 4 3
R R 4R R R 3R , R R R
1 1 1 3
0 4 3 11
0 1 3 8
0 3 6 3
1 1 1 3
R 4R R
0 4 3 11
0 0 15 21
R 4R 3R
0 0 15 21
1 1 1 3
0 4 3 11
R R R
0 0 15 21
0 0 0 0
→ − → − → −
− −
− − − − −
→ −
− −
− −
→ −
− −
→ +
− −
(A : B A 3 no. of variables ) ( )
Unique solution exists
ρ = ρ = =
∴
5. The value of the dot product of the eigenvectors corresponding to any pair of different eigen
values of a 4-by-4 symmetric positive definite matrix is ______________.
Answer: (0)
Exp: ( The eigen vectors corresponding to distinct eigen values of real symmetric matrix are
orthogonal)
6. Let the function
( ) ( ) ( ) ( )
( ) ( ) ( )
sin cos tan
f sin cos tan 6 6 6
sin cos tan 3 3 3
θ θ θ
θ = π π π
π π π
Where ,
6 2
π π θ =∈ and f '(θ) denote the derivative of f with respect to θ . Which of the
following statement is / are TRUE?
(I) There exists ,
6 3
π π θ∈ such that f ' 0 (θ =) .
(II) There exists ,
6 3
π π θ∈ such that f ' 0 (θ ≠) .
(A) I only (B) II only (C) Both I and II (D) Neither I nor II
Answer: (C)
Exp: (By Mean value theorem)
7. Consider the following Boolean expression for F:
F P,Q,R,S PQ PQR PQRS ( ) = + +
The minimal sum-of products form of F is
(A PQ QR QS ) + + (B P Q R S ) + + +
(C P Q R S ) + + + (D PR PRS P ) + +
Answer: (A)
Exp: PQ PQR PQRS + +
( )
( ) ( )( ) ( )( )
( )
( ) ( )
PQ PQ R RS
PQ PQ R R R S A BC A B A C
PQ PQ R S R R 1
Q P P R S
= + +
= + + + + = + +
= + + + =
= + +
∵
∵
(( )( )) ( )( )
( )
Q P P P R S A BC A B A C
Q P R S P P 1
PQ QR QS
= + + + + = + +
= + + + =
= + +
∵
∵
8. The base (or radix) of the number system such that the following equation holds
is____________.
312 13.1
20
=
Answer: (5)
Exp: Let ‘x’ be the base or radix of the number system
( )
o 2
o 1
o
2
2 2
2 2
2
2 x 1 x 3 x 3 x 1 x 1 x
0 x 2 x
2 x 3x 1 3 x
2x x
3x x 2 3x x 1
2x x
3x x 2 6x 2x 2
x 5x 0
x x 5 0
x 0 or x 5
× + × + × −
= × + × + ×
× + ×
+ +
⇒ = + +
+ + + +
⇒ =
⇒ + + = + +
⇒ − =
⇒ − =
⇒ = =
As base or radix of a number system cannot be zero, here x 5 =
9. A machine has a 32-bit architecture, with 1-word long instructions. It has 64 registers, each of
which is 32 bits long. It needs to support 45 instructions, which have an immediate operand
in addition to two register operands. Assuming that the immediate operand is an unsigned
integer, the maximum value of the immediate operand is ____________.
Answer: (16383)
Exp: 1 Word 32 bits =
Each instruction has 32 bits
To support 45 instructions, opcode must contain 6-bits
Register operand1 requires 6 bits, since the total registers are 64.
Register operand 2 also requires 6 bits
14-bits are left over for immediate Operand Using 14-bits, we can give maximum 16383,
Since ( )
14 2 16384 from 0 to 16383 =
6 6 6 14
32 bits
opcode Re g opd 1 Re g opd 2
immediate
opnd
10. Consider the following program in C language:
( )
( )
( )
# include stdio.h
main
{
int i;
int * pi &i;
scanf "%d", pi ;
pr int f "%d \ n", i 5 ;
}
< >
=
+
Which one of the following statements is TRUE?
(A) Compilation fails.
(B) Execution results in a run-time error.
(C) On execution, the value printed is 5 more than the address of variable i.
(D) On execution, the value printed is 5 more than the integer value entered.
Answer: (D)
Exp: pi contains the address of i. So scanf("%d",pi) places the value entered in console into
variable i.e So printf("%d\n",i+5),prints 5 more than the value entered in console.
11. Let G be a graph with n vertices and m edges. What is the tightest upper bound on the
running time of Depth First Search on G, when G is represented as an adjacency matrix?
(A) θ(n) (B) θ + (n m) (C) ( )
2
θ n (D) ( )
2
θ m
Answer: (C)
Exp: DFS visits each vertex once and as it visits each vertex, we need to find all of its neighbours
to figure out where to search next. Finding all its neighbours in an adjacency matrix requires
O(V ) time, so overall the running time will be O(V2
).
12. Consider rooted n node binary tree represented using pointers. The best upper bound on the
time required to determine the number of sub trees having exactly 4 nodes is ( )
a b 0 n log n .
Then the value of a + 10b is_______
Answer: 1
Exp: int print_subtrees_size_4(node *n)
{
int size=0;
if(node==null)
return 0;
size=print_subtrees_size_4(node->left)+print_subtrees_size_4(node->right)+1;
if(size==4)
printf("this is a subtree of size 4");
return size;
}
The above function on taking input the root of a binary tree prints all the subtrees of size 4 in
O(n) time
so a=1 , b=0 and then a+10b=1
13. Consider the directed graph given below.
Which one of the following is TRUE?
(A) The graph does not have any topological ordering
(B) Both PQRS and SRQP are topological orderings
(C) Both PSRQ and SPRQ are topological orderings.
(D) PSRQ is the only topological ordering.
Answer: (C)
Exp: Topological ordering of a directed graph is a linear ordering of its vertices such that for every
directed edge uv from vertex u to vertex v, u comes before v in the ordering. Topological
ordering is possible iff graph has no directed cycles.
(A) As the given graph doesn’t contain any directed cycles, it has at least one topological
ordering. So option (A) is false
(B) PQRS cannot be topological ordering because S should come before R in the ordering as
there is a directed edge from S to R.
SRQP cannot be topological ordering, because P should come before Q in the ordering as
there is a directed edge from P to Q
(C) PSRQ and SPRQ are topological orderings as both of then satisfy the above mentioned
topological ordering conditions.
(D) PSRQ is not the only one topological ordering as SPRQ is other possibility
14. Let P be a quick sort program to sort numbers in ascending order using the first element as
the pivot. Let t1 and t2 and t2 be the number of comparisons made by P for the inputs [1 2 3 4
5] and [4 1 5 3 2] respectively. Which one of the following holds?
(A) t1 =5 (B) t1 < t2 (C) t1>t2 (D) t1 = t2
Answer: (C)
Exp: Partition algorithm for quick sort
( ) [ ]
[ ] [ ]
[ ]
[ ] [ ]
[ ] [ ]
Partition A,P,q // A P,.....q
x A P // pivot A P
i P
for j P 1 to q
do if A j x
then i i 1
exchange A i A j
exchangeA P A i
← =
←
= +
≤
← +
↔
↔
return i [returning where pivot element is there after partitioning]
Recursively call the above algorithm for the two sub arrays [elements before and after pivot
element] to complete the sorting.
P Q
R S
x pivot
1 2 3 4 5
i j
=
2 1 ? NO ≤
Pivot x A B[ ]
1 2 3 4 5
i j
= =
3 2 ? NO ≤
1 2 3 4 5
i j 3 1 ? NO ≤
1 2 3 4 5
i j 4 2 ? NO ≤
1 2 3 4 5
i j 4 1 ? NO ≤
1 2 3 4 5
i j 5 2 ? NO ≤
1 2 3 4 5
i j 5 1 ? NO ≤
exchange A P & A J [ ] [ ]
exchange A P & A i [ ] [ ]
x Pivot A P[ ]
1 2 3 4 5
i j
= =
4 3 ? NO ≤
x Pivot
1 2 3 4 5
i j
=
5 4 ? NO ≤
1 2 3 4 5
i j 5 3 ? NO ≤
exchange A P & A i [ ] [ ]
exchange A P & A i [ ] [ ]
1 2 3 4 5 ∴ Total 10 conparisons
Pivot ≥Pivot
1 2 3 4 5
Pivot ≥Pivot
1 2 3 4 5
Pivot ≥Pivot
Call recursively
for this
1 2 3 4 5
Pivot ≥ Pivot Call recursively
for this subarray
[ ]
[ ] [ ]
[ ] [ ]
x pivot A P
4 1 5 3 2
i j 1 4?Yes
i i 1 exchange A i & A j & increment j
4 1 5 3 2
i j 5 4?NO
4 1 5 3 2
i j 3 4?Yes
i i 1 exchange A i & A j & increment j
4 1 3 5 2
i J 2 4?Yes
= =
≤
← +
≤
≤
← +
≤
[ ] [ ]
i i 1
4 1 3 2 5
i j
exchange A P & A i
← + ( )
[ ] [ ]
x pivot A P
2 1 3 | 4 | 5
i j 1 2 ? yes
2 1 3 | 4 | 5
i j 3 2 ? NO
exchange A P & A i
= =
≤
≤
∴6 conparisons
15. Which one of the following is TRUE?
(A) The language L = { }
n n a b | n 0 ≥ is regular.
(B) The language L = { }
n
a | n is prime is regular.
(C) The language L = { w | w has 3k 1b's + for some k ∈ N with Σ = {a,b} } is regular.
(D) The language L = { { }}
* ww | w with 0,1 ∈Σ Σ = is regular.
Answer: (C)
Exp: (A) { }
n n L a b n 0 = ≥ is a CFL but not regular, it requires memory for the representation
(B) { }
n L a n is prime = is neither regular nor CFL
(C) L w | w has 3K 1 b's for some k N with = + ∈ { }
Σ = {a,b}
is a regular language, since the total count of b’s are multiple of 3 plus one. The regular
expression is a * ba * a *ba *ba * ba * * a * ba * ba * ba * *a * ba * ( ) +( )
(D) L ww | w * with 0,1 = ∈Σ Σ = { { }} is neither regular nor CFL
1 2 3 4 5
Pivot
2 1 3 4 5
≤Pivot Pivot ≥Pivot
16. Consider the finite automaton in the following figure.
What is the set of reachable states for the input string 0011?
(A) {q ,q ,q 0 1 2 } (B) {q ,q 0 1} (C) {q ,q ,q ,q 0 1 2 3} (D) {q3}
Answer: (A)
Exp: δ = δ (q ,0011 q ,011 0 0 ) ( )
( )
( ) { }
( ) ( )
{ } { }
{ }
0
0 1
0 1
0 1 2
0 1 2
q ,11
q ,q ,1
q ,1 q ,1
q ,q q
q ,q ,q
= δ
= δ
= δ ∪ δ
= ∪
=
17. Which one of the following is FALSE?
(A) A basic block is a sequence of instructions where control enters the sequence at the
beginning and exits at the end.
(B) Available expression analysis can be used for common subexpression elimination.
(C) Live variable analysis can be used for dead code elimination
(D) x 4*5 x 20 = ⇒ = is an example of common subexpression elimination
Answer: (D)
Exp: x 4 5 x 20 = × ⇒ = is not an example of common sub-expression but it is constant folding. In
constant folding expression consisting of constants will be replaced by their final value at
compile time, rather than doing the calculation in run-time.
18. Match the following
(1) Waterfall model (a) Specifications can be developed
(2) Evolutionary model (b) Requirements compromises are inevitable
(3) Component based software (c) Explicit recognition of risk
(4) Spiral development (d) Inflexible partitioning of the project into stages
(A) 1-a, 2-b, 3-c, 4-d (B) 1-d, 2-a, 3-b, 4-c
(C) 1-d, 2-b, 3-a, 4-c (D) 1-c, 2-a, 3-b, 4-d
Answer: (B)
Exp: The main drawback of the waterfall model is the difficulty of accommodating change after
the process is underway. One phase has to be complete before moving onto the next phase.
Inflexible partitioning of the project into distinct stages in waterfall model makes it difficult
to respond to changing customer requirements.
Evolutionary software models are iterative. They are characterized in manner that enables the
software engineers to develop increasingly more complete version of software.
In Spiral model, Development can be divided in to smaller parts and more risky parts can be
developed earlier which helps better risk management.
0,1
0
q 1
q 2
q 3
q
1 0,1 0,1
1
19. Suppose a disk has 201 cylinders, numbered from 0 to 200. At some time the disk arm is at
cylinder 100, and there is a queue of disk access requests for cylinders 30, 85, 90, 100, 105,
110, 135 and 145. If Shortest-Seek Time First (SSTF) is being used for scheduling the disk
access, the request for cylinder 90 is serviced after servicing ____________ number of
requests.
Answer: (3)
Exp:
Request for cylinder is served after serving 3 requests (100,105 and 110)
20. Which one of the following is FALSE?
(A) User level threads are not scheduled by the kernel.
(B) When a user level thread is blocked, all other threads of its process are blocked.
(C) Context switching between user level threads is faster than context switching between
kernel level threads.
(D) Kernel level threads cannot share the code segment.
Answer: (D)
Exp: User threads are supported above the kernel and a managed without kernel support. The
thread function library to implement user level threads usually runs on top of the system in
user mode. Thus these threads with in a process are invisible to the operating system. Since
the kernel is unaware of the existence of such threads; when one user level thread is blocked
in the kernel all other threads of its process are blocked. So options (A) and (B) are true
(C) The OS is aware of kernel level threads. Kernel threads are scheduled by the OS’s
scheduling algorithms and require a “lightweight” context switch to switch between
(that is, registers, PC and SP must be changed, but the memory context remains the same
among kernel threads in the (same process). User level threads are much faster to switch
between as there is not context switch
(D) False
Kernel level threads within the same process share code section, data section and other
operating system resources such as open files and signals.
100
105
110
90
85
135
145
30
21. Consider the relation scheme R = (E, F, G, H, I, J, K, L, M, N) and the set of functional
dependencies {{E,F}→ {G},{F}→ {I,J , E,H K,L M } { } → → { } ( ) , {K M , } →{ } }
{L N } →{ } on R. What is the key for R?
(A) {E, F} (B) {E, F, H} (C) {E, F, H, K, L} (D) {E}
Answer: (B)
Exp: R EFGHI,JKLMN ( )
F {
EF G
F IJ
EH KL
K M
L
}
=
→
→
→
→
→ Ν
( ) EF EFGIJ, E & F +
= Together functionally derive GIJ and if we observe given FDs, H
can’t be determined by any other attributes. So H must be part of all the (candidate) keys. H
along with E determines K and L, K & L functionally determine M and N respectively.
( ) EFH EFGIJHKLMN + ∴ =
∴ EFH is the only candidate for key.
22. Given the following statements:
S1: A foreign key declaration can always be replaced by an equivalent check
assertion in SQL
S2: Given the table R(a,b,c) where a and b together form the primary key, the following is a
valid table definition.
CREATE TABLE S (
a INTEGER,
d INTEGER,
e INTEGER,
PRIMARY KEY (d),
FOREIGN KEY (a) references R)
Which one of the following statements is CORRECT?
(A) S1 is TRUE and S2 is a FALSE (B) Both S1 and S2 are TRUE
(C) S1 is FALSE and S2 is a TRUE (D) Both S1 and S2 are FALSE
Answer: (D)
Exp: S1: Manager (Name, DeptID)
Department (DeptName, Deptid)
In given relation Manager DeptID is a foreign key referencing Deptid (P.K) of relation
Department.
Let’s declare the foreign key by an equivalent check assertion as follows:-
CREATE TABLE Manager (
Name Varchar (10)
DeptID INT (6) check (DeptID IN ( select Deptid from Department)),
PRIMARY KEY (Name)
);
The above use of check assertion is good to declare the foreign key as far as insertion is
considered for relation manager (will not insert any tuple in Manager containing such DeptID
value which is not present in any tuple of Department).
But the above declaration will fail to implement changes done in Department relation in
terms of deletion & updation. For an instance if a deptid present in Department gets deleted,
then respective reference in Manager should also be deleted.
∴ S1 is false.
S2: The given table definition is not valid due to invalid foreign key declaration. Attribute a
is declared as foreign key which is a single valued attribute and it is referencing the primary
key (ab) of relation R (a, b, c), which is a composite key.
A single value attribute cannot refer a composite key.
4 S2 is false.
23. Consider the following three statements about link state and distance vector routing protocols,
for a large network with 500 network nodes and 4000 links
[S1] The computational overhead in link state protocols is higher than in distance vector
protocols.
[S2] A distance vector protocol (with split horizon) avoids persistent routing loops, but not
a link state protocol.
[S3] After a topology change, a link state protocol will converge faster than a distance
vector protocol.
Which one of the following is correct about S1, S2, and S3?
(A) S1, S2, and S3 are all true (B) S1, S2, and S3 are all false.
(C) S1 and S2 are true, but S3 is false (D) S1 and S3 are true, but S2 is false.
Answer: (D)
Exp: Statement S1
The Distance Vector routing protocols rely on the information from their directly connected
neighbours in order to calculate and accumulate route information. Distance Vector routing
protocols require very little overhead as compared to Link State routing protocols as
measured by memory and processor power while the Link State routing protocols do not rely
solely on the information from the neighbours or adjacent router in order to calculate route
information. Instead, Link State routing protocols have a system of databases that they use in
order to calculate the best route to destinations in the network. This is TRUE
Statement S3
Distance Vector exchanges the routing updates periodically whether the topology is change
or not, this will maximize the convergence time which increases the chance of routing loops
while the Link State routing protocols send triggered change based updates when there is a
topology change. After initial flood, pass small event based triggered link state updates to all
other routers. This will minimize the convergence time that’s why there is no chance of
routing loops. This is TRUE.
24. Which one of the following are used to generate a message digest by the network security
protocols?
(P) RSA (Q) SHA-1 (R) DES (S) MD5
(A) P and R only (B) Q and R only (C) Q and S only (D) R and S only
Answer: (C)
Exp: RSA and DES are for Encryption where MD5 and SHA – 1 are used to generate Message
Digest.
25. Identify the correct order in which the following actions take place in an interaction between
a web browser and a web server.
1. The web browser requests a webpage using HTTP.
2. The web browser establishes a TCP connection with the web server.
3. The web server sends the requested webpage using HTTP.
4. The web browser resolves the domain name using DNS.
(A) 4,2,1,3 (B) 1,2,3,4 (C) 4,1,2,3 (D) 2,4,1,3
Answer: (A)
Exp: First of all the browser must now know what IP to connect to. For this purpose browser takes
help of Domain name system (DNS) servers which are used for resolving hostnames to IP
addresses. As browser is an HTTP client and as HTTP is based on the TCP/IP protocols, first
it establishes a TCP connection with the web server and requests a webpage using HTTP, and
then the web server sends the requested webpage using HTTP. Hence the order is 4,2,1,3
Q.No. 26 – 55 Carry Two Marks
26. Consider a token ring network with a length of 2km having 10 stations including a
monitoring station. The propagation speed of the signal is 2 x 108
m/s and the token
transmission time is ignored. If each station is allowed to hold the token for 2 μsec, the
minimum time for which the monitoring station should wait (in μsec) before assuming that
the token is lost is _______.
Answer: (28μs to 30μs)
Exp: Given Length (d) = 2 Km
No. of Stations (m) = 10
Propagation Speed (v) = 2 × 108
m/s
THT = 2μs
So, Max. TRT = TP in the Ring + No. of Active Stations * THT
= 10 × 10-6 + 10 × 2 × 10-6
= 30 μs
27. Let the size of congestion window of a TCP connection be 32 KB when a timeout occurs.
The round trip time of the connection is 100 msec and the maximum segment size used is
2kB. The time taken (in msec) by the TCP connection to get back to 32KB congestion
window is ______
Answer: (1100 to 1300)
Exp: Given that at the time of Time Out, Congestion Window Size is 32KB and RTT = 100ms
When Time Out occurs, for the next round of Slow Start, Threshold = (size of Cwnd) / 2
It means Threshold = 16KB
Slow Start
2KB
1RTT
4KB
2RTT
8KB
3RTT
16KB ----------- Threshold reaches. So Additive Increase Starts
4RTT
18KB
5RTT
20KB
6RTT
22KB
7RTT
24KB
8RTT
26KB
9RTT
28KB
10RTT
30KB
11RTT
32KB
So, Total no. of RTTs = 11 → 11 * 100 = 1100
28. Consider a selective repeat sliding window protocol that uses a frame size of 1 KB to send
data on a 1.5 Mbps link with a one-way latency of 50 msec. To achieve a link utilization of
60%, the minimum number of bits required to represent the sequence number field is
________.
Answer: (5)
Exp:
p
Given L 1KB
B 1.5Mbps
T 50ms
60%
=
=
=
η =
Efficiency formula for SR protocol is
p
x
W 60 W T
a
1 2a 100 1 2a T
η = ⇒ = =
+ +
∵
3
x 6
L 8 10 T 5.3ms
B 1.5 10
×
= = =
×
p
x
T 50 500 a 9.43
T 5.3 53
= = = =
60 W W 11.9 12
100 19.86
⇒ = ⇒ = ≈
⇒ W 2 12 2 24 2 24 2 n 5 n 1 n n 5 −
= = ⇒ = ⇒ = ≈ ⇒ =
29. Consider the following four schedules due to three transactions (indicted by the subscript)
using read and write on a data item x, denoted r (x) and w (x) respectively. Which one of
them is conflict serializable?
(A) r1 (x) ; r2 (x) ; w1 (x) ; r3(x) ; w2 (x) (B) r2 (x) ; r1 (x) ; w2 (x) ; r3(x) ; w1 (x)
(C) r3 (x) ; r2 (x) ; r1 (x) ; w2(x) ; w1 (x) (D) r2 (x) ; w2 (x) ; r3 (x) ; r1(x) ; w1 (x)
Answer: (D)
Exp: If there is a cycle in precedence graph, then the schedule is not conflict serializable.
(A) (B)
Not conflict serializable not conflict serializable
(C) (D)
Not conflict serializable it is conflict equivalent to
2 3 1
3 2 1
T T T &
T T T
→ →
→ →
T1 T2
T3
T1 T2
T3
T2
T3
T1
T1 T2
T3
T1 T2
T3
30. Given the following two statements:
S1: Every table with two single-valued attributes is in 1NF, 2NF, 3NF and BCNF
S2 : AB C, D E, E C → → → is a minimal cover for the set of functional
dependencies AB C, D E, AB E,E C → → → →
Which one of the following is CORRECT?
(A) S1 is TRUE and S2 is FALSE. (B) Both S1 and S2 are TRUE.
(C) S1 is FALSE and S2 is TRUE. (D) Both S1 and S2 are FALSE.
Answer: (A)
Exp: S : True 1
Consider any table R with two attributes R A.B ( )
The possible FD sets are
F { 1
A B
}
Key : A and is in BCNF
=
→
F { 2
B A
}
Key : B and is in BCNF
=
→
F { 3
A B
B A
}
Key : A & B It is in BCNF
=
→
→
F { 4
}
Key : AB and is in BCNF
=
If a table is in BCNF it is also in 1NF, 2NF and 3NF also
S : False 2
First FD set cannot cover second FD set because in second FD set AB can functionally derive
E but that is not happing in first FD set.
31. An operating system uses the Banker’s algorithm for deadlock avoidance when managing the
allocation of three resource types X, Y, and Z to three processes P0, P1, and P2. The table
given below presents the current system state. Here, the Allocation matrix shows the current
number of resources of each type allocated to each process and the Max matrix shows the
maximum number of resources of each type required by each process during its execution.
There are 3 units of type X, 2 units of type Y and 2 units of type Z still available. The system
is currently in a safe state. Consider the following independent requests for additional
resources in the current state:
REQ1: P0 requests 0 units of X, 0 units of Y and 2 units of Z
REQ2: P1 requests 2 units of X, 0 units of Y and 0 units of Z
Allocation Max
X Y Z
0 0 1
3 2 0
2 1 1
X Y Z
8 4 3
6 2 0
3 3 3
P0
P1
P2
Which one of the following is TRUE?
(A) Only REQ1 can be permitted.
(B) Only REQ2 can be permitted.
(C) Both REQ1 and REQ2 can be permitted.
(D) Neither REQ1 nor REQ2 can be permitted.
Answer: (B)
Exp: REQ1
Once P0
is allocated with (0,0,2) , the status of the system will be as follows
Allocation Max Need Available
X Y Z
0 0 3
3 2 0
2 1 1
X Y Z
8 4 3
6 2 0
3 3 3
X Y Z
8 4 0
3 0 0
1 2 2
X Y Z
3 2 0
With available ( ) 1
3,2,0 only P can be served. Once P1
is executed, available will be (6,4,0) ,
with (6,4,0) we can’t serve either P or P 0 2 . Hence there is no safe sequence. Hence REQ1
can’t be permitted.
REQ2
Once P1
is allocated with (2,0,0) , the status of the system will be as follows
Allocated Max Need Available
0
1
2
P
P
P
X Y Z
0 0 1
5 2 0
2 1 1
X Y Z
8 4 3
6 2 0
3 3 3
X Y Z
8 4 2
1 0 0
1 2 2
X Y Z
1 2 2
With available (1,2,2), we can serve either P or P 1 2 .
If we serve P1
then the safe sequence is P ,P ,P 1 2 0 . If we serve P2
then the safe sequence is
P ,P ,P 2 1 0 . As true is at least one safe sequence we can permit REQ2.
32. Consider the following set of processes that need to be scheduled on a single CPU. All the
times are given in milliseconds
Process Name Arrival Time Execution Time
A 0 6
B 3 2
C 5 4
D 7 6
E 10 3
Using the shortest remaining time first scheduling algorithm, the average process turnaround
time (in msec) is ____________________.
Answer: (7.2)
Exp:
A B A C E D
0 3 5 8 12 15 21
(8 0 5 3 12 5 21 7 15 10 ) ( ) ( ) ( ) ( )
Average turn around time
5
36 7.2ms
5
− + − + − + − + −
=
= ⇒
33. Assume that there are 3 page frames which are initially empty. If the page reference string 1,
2, 3, 4, 2, 1, 5, 3, 2, 4, 6, the number of page faults using the optimal replacement policy is
___________
Answer: (7)
Exp:
1 2 3 4 2 1 5 3 2 4
3 4 4 4 4 4 4 4 4
2 2 2 2 2 2 2 2 2 6
1 1 1 1 1 1 5 3 3 3 3
F F F F H H F F H H F
7 page faults
34. A canonical set of items is given below
s L. R
Q R.
→ >
→
On input symbol < the set has
(A) a shift-reduce conflict and a reduce-reduce conflict.
(B) a shift-reduce conflict but not a reduce-reduce conflict.
(C) a reduce-reduce conflict but not a shift-reduce conflict.
(D) neither a shift-reduce nor a reduce-reduce conflict.
Answer: (D)
Exp:
>
From above diagram, we can see that there is no shift- reduce or reduce-reduce conflict.
→ >
→
S L . R
Q R.
S L . R → >
old I
new I
35. Let L be a language and L be its complement. Which of the following is NOT a viable
possibility?
(A) Neither L nor L is recursively enumerable (r.e.).
(B) One of L and L is r.e. but not recursive; the other is not r.e.
(C) Both L and L are r.e. but not recursive.
(D) Both L and L are recursive.
Answer: (C)
Exp: Recursive languages are closed under complement.
If a language L is recursive enumerable but not recursive then its complement is not a
recursive enumerable, so both L and L are recursive enumerable but not recursive is not a
viable possibility.
36. Which of the regular expressions given below represent the following DFA?
I) 0*1(1+00*1)*
II) 0*1*1+11*0*1
III) (0+1)*1
(A) I and II only (B) I and III only
(C) II and III only (D) I, II, and III
Answer: (B)
Exp: Given DFA will accept all the strings over ε ={0,1} which are ending with 1.
0*1 1 00*1 * and 0 1 *1, ( + + ) ( ) are the regular expressions for ending with 1.
37. There are 5 bags labelled 1 to 5. All the coins in a given bag have the same weight. Some
bags have coins of weight 10 gm, others have coins of weight 11 gm. I pick 1, 2, 4, 8, 16
coins respectively from bags 1 to 5. Their total weight comes out to 323 gm. Then the product
of the labels of the bags having 11 gm coins is ___.
Answer: 12
Exp: Let the weight of coins in the respective bags (1 through 5) be a,b,c,d and e-each of which
can take one of two values namely 10 or 11 (gm).
Now, the given information on total weight can be expressed as the following equation:
1.a+2.b+4.c+8.d+16.e = 323
⇒ a must be odd ⇒ a = 11
The equation then becomes:
11+2.b+4.c+8.d+16.e = 323
0 0 1
1
⇒ 2.b+4.c+8.d+16.e = 312
⇒ b+2.c+4.d+8.e = 156
⇒ b must be even ⇒ b = 10
The equation then becomes:
10+2.c+4.d+8.e = 156
⇒ 2.c+4.d+8.e = 146
⇒ c+2.d+4.e = 73
⇒ c must be odd ⇒ c = 11
The equation now becomes:
11+2.d+4.e = 73
⇒ 2.d+4.e = 62
⇒ d+2.e = 31
⇒ e = 11 and e = 10
Therefore, bags labelled 1, 3 and 4 contain 11 gm coins ⇒ Required Product = 1*3*4* = 12.
38. Suppose a polynomial time algorithm is discovered that correctly computes the largest clique
in a given graph. In this scenario, which one of the following represents the correct Venn
diagram of the complexity classes P, NP and NP Complete (NPC)?
Answer: (D)
Exp: The most important open question in complexity theory is whether the P = NP , which asks
whether polynomial time algorithms actually exist for NP-complete and all NP problems (
since a problem “C” is in NP-complete, iff C is in NP and every problem in NP is reducible
to C in polynomial time). In the given question it is given that some polynomial time
algorithm exists which computes the largest clique problem in the given graph which is
known NP-complete problem. Hence P=NP=NP-Complete.
(A)
P
NPC
NP
(B)
P NP
NPC
(B)
NPC P NP =
(D)
P NP NPC = =
CS-GATE-2014 PAPER-01| www.gateforum.com
India’s No.1 institute for GATE Training 1 Lakh+ Students trained till date 65+ Centers across India
24
39. The minimum number of comparisons required to find the minimum and the maximum of
100 numbers is _________________.
Answer: (148)
Exp: From the list of given n numbers [say n is even],
Pick up first two elements, compare them
assign Current min min of two numbers
Current max max of two numbers
− =
− =
From the remaining n 2 − numbers, take pairs wise and follow this process given below.
1. Compare two elements
Assign min = min of two numbers
max = max of two numbers
2. Compare min and current - min
Assign current min min current min,min − = − { }
3. Compare max and current - max
Assign current max max current max,max − = − { }
Repeat above procedure for all the remaining pairs of numbers. We can observe that each of
pair requires 3 comparisons
1. for finding min and max
2. For updating current – min
3. for updating current – max
But for initial pair we need only one comparison not 3.
3 n 2 ( ) 3n 3n total number of comparisons 1 3 1 2
2 2 2
−
∴ = + = − + = −
Here n 100, = so number of comparisons = 148.
40. Consider a hash table with 9 slots. The hash function is h k k mod 9. ( ) = The collisions are
resolved by chaining. The following 9 keys are inserted in the order: 5, 28, 19, 15, 20, 33, 12,
17, 10. The maximum, minimum, and average chain lengths in the hash table, respectively,
are
(A) 3, 0, and 1 (B) 3, 3, and 3 (C) 4, 0, and 1 (D) 3, 0, and 2
Answer: (A)
Exp:
Maximum & minimum chain lengths are 3 & 0 respectively
0 3 1 1 0 1 2 0 1 Average chain length 1
9
∴
+ + + + + + + +
= =
41. Consider the following C function in which size is the number of elements in the array E:
int MyX(int *E, unsigned int size)
{
int Y = 0;
int Z;
int i, j, k;
for(i = 0; i < size; i++)
Y = Y + E[i];
for(i = 0; i < size; i++)
for(j = i; j < size; j++)
{
Z = 0;
for(k = i; k <= j; k++)
Z = Z + E[k];
if (Z > Y)
Y = Z;
}
return Y;
}
The value returned by the function MyX is the
(A) maximum possible sum of elements in any sub-array of array E.
(B) maximum element in any sub-array of array E.
(C) sum of the maximum elements in all possible sub-arrays of array E.
(D) the sum of all the elements in the array E.
Answer: (A)
0
1
2
3
4
5
6
7
8
28 19 10
20
12
5
15 33
17
Exp: int Myx int * E, unsin ged int sixe ( )
( )
[ ]
( )
( )
( )
[ ]
{
int Y 0;
int z;
int i, j,k;
for i 0;i size;i Calculates sum of the elements
Y Y E i of the array E and stores it in Y
for i 0; i size; i
for j i; j size; j
{ calculates the sum of elements o
z 0;
for k i;k j; k
z z E k ;
=
= < + +
= +
= < + +
= < + +
=
= <= + +
= +
( )
f
all posible subarrays of E
if z Y Checks whether sum of elements of each subarray
Y z; is greaer than the sum of elements of array if so,that sum
} is assigned to Y, if not 'Y' will be the sum of elements of
return Y; complete array
}
> →
=Ultimately returns the maximum possible sum of elements in any sub array of given array E.
42. Consider the following pseudo code. What is the total number of multiplications to be
performed?
D= 2
for i = 1 to n do
for j = i to n do
for k = j + 1 to n do
D = D * 3
(A) Half of the product of the 3 consecutive integers
(B) One-third of the product of the 3 consecutive integers.
(C) One-sixth of the product of the 3 consecutive integers.
(D) None of the above.
Answer: (C)
Exp:
( )
i 1, j 1, k 2 to n n 1 times
i 1, j 2, k 3 to n n 2 times
i 1, j 3, k 4 to n n 3 times
n 1 times
:
i 1, j n 2, k n 1 to n 2 times
i 1, j n 1, k n to n 1 time
= = = ⇒ −
= = = ⇒ −
= = = ⇒ −
∑ −
= = − = − ⇒
= = − = ⇒
( )
i 2, j 2,k 3 to n n 2 times
i 2, j 3,k 4 to n n 3 times
: : n 2 times
: :
i 2, j n 1,k n to n 1 time
:
:
i n 1, j n 1,k n to n 1 time } 1 times
= = = ⇒ −
= = = ⇒ −
∑ −
= = − = ⇒
= − = − = ⇒ ∑
( )
( ) ( ) ( )
( )
( )( ) ( ) ( )( )( )
1
2 3 n 1
S
S S S
n 1
i
i 1
2
Total number of multiplications
1 2 3 ...... n 1
1 1 2 1 2 3 .... 1 2 3 ..n 1
n n 1
S
2
1 1
n n
2 2
1 1 n n 1 2n 1 n n 1 n 1 n n 1
2 6 2 2 6
−
↓
↓ ↓ ↓
−
=
∴
⇒ ∑ + ∑ + ∑ + ∑ −
= + + + + + + + + + + −
−
= = ∑
= ∑ − ∑
+ + + − +
= − =
∑
43. Consider a 6-stage instruction pipeline, where all stages are perfectly balanced. Assume that there is no cycle-time overhead of pipelining. When an application is executing on this 6-stage pipeline, the speedup achieved with respect to non-pipelined execution if 25% of the instructions incur 2 pipeline stall cycles is ______________________.
Answer: (4)
Exp: For 6 stages, non- pipelining takes 6 cycles.
There were 2 stall cycles for pipelining for 25% of the instructions
25 So pipe line time 1 2
100
3
1.5
2
Non pipeline time 6 Speed up 4
Pipeline time 1.5
= +
= =
−
= = =
44. An access sequence of cache block addresses is of length N and contains n unique block
addresses. The number of unique block addresses between two consecutive accesses to the
same block address is bounded above K. What is the miss ratio if the access sequence is
passed through a cache of associativity A k ≥ exercising least-recently-used replacement
policy?
(A) n/N (B) l/N (C) 1/A (D) k/n
Answer: (A)
45. Consider the 4-to-1 multiplexer with two lines S1 and S0 given below.
The minimal sum of-products form of the Boolean expression for the output F of the
multiplexer is
(A) PQ QR PQR + + (B) PQ PQR PQR PQR + + +
(C) PQR PQR QR PQR + + + (D) PQR
Answer: (A)
Exp: PQ.O PQ.1 PQ.R PQR + + +
= + + PQ PQ.R PQR
Hence the minimized expression is PQ QR PQR + +
46. The function f(x) = x sin x satisfies the following equation. f"(x) + f(x) +tcosx = 0. The value
of t is______.
Answer: -2
Exp: Given f " x f x t cos x 0 ( ) + + = ( )
and f (x) xsin x
f ' x x cos x sin x
f " x x sin x cos x cos x
2cos x xsin x
2cos x f x
2cos x f x f x t cos x 0
2cos x t cos x t 2
=
= +
= − + +
= −
= −
∴ − + + =
⇒ =− ⇒ = −
0
1
R
R
0
1
2
3
1
s 0
s
4 to 1
Multiplexer
− −
F
P Q
PQ QR QR QR QR
P 1
P
1
1 1
QR
PQR
47. A function f(x) is continuous the interval [0,2]. It is known that f(0) = f(2) = -1 and f(1) = 1.
Which one of the following statements must be true?
(A) There exists a y in the interval (0,1) such that f(y) = f(y + 1)
(B) For every y in the interval (0,1), f(y) = f(2 - y)
(C) The maximum value of the function in the interval (0.2) is 1
(D) There exists a y in the interval (0,1) such that f(y) =f(2 – y)
Answer: (A)
Exp: Define g(x) =f(x)-f(x+1) in [0,1]. g(0) is negative and g(1) is positive. By intermediate value
theorem there is y€(0,1) such that g(y)=0
That is f(y) =f(y+1).
Thus answer is (a)
48. For fair six-sided dice are rolled. The probability that the sum of the results being 22is
X
1296. The value of X is _________
Answer: (10)
Exp: 22 occurred in following ways
6 6 6 4 4ways
6 6 5 5 6ways
→
→
Required probability = 6 4 10 x 10
2296 2296
+
= ⇒ =
49. A pennant is a sequence of numbers, each number being 1 or 2. An n-pennant is a sequence
of numbers with sum equal to n. For example, (1,1,2) is a 4-pennant. The set of all possible 1-
pennants is {(1)}, the set of all possible 2-pennants is {(2), (1,1)}and the set of all 3-pennants
is {(2,1), (1,1,1), (1,2)}. Note that the pennant (1,2) is not the same as the pennant (2,1). The
number of 10- pennants is ______________.
Answer: (89)
Exp: No twos: 1111111111⇒1 pennant
Single two: 211111111⇒9!/8!1! = 9 pennants
Two twos: 22111111⇒8!/6!.2! = 28
Three twos: 2221111⇒7!/3!.4! = 35
Four twos: 222211⇒6!/4!.2! = 15
Five twos: 22222⇒1
Total = 89 pennants.
50. Let S denote the set of all functions { } { } 4
f : 0,1 0,1 → . Denote by N the number of functions
from S to the set {0,1}. The value of log2 log2 N is______.
Answer: (16)
Exp: The number of functions from A to B where size of A = |A| and size of B = |B| is |B||A|
{0,1}4
= {0,1}X{0,1}X{0,1}X{0,1} = 16
|S| = 216
N = 2|S|
loglog N = log log 2|S| = log |S| = log 216 = 16
51. Consider an undirected graph G where self-loops are not allowed. The vertex set of G is {i,
f): 1 ≤ i ≤ 12, 1 ≤ j ≤ 12}. There is an edge between (a,b) and (c,d) if a c 1 − ≤ and
b d 1 − ≤ The number of edges in the graph is _____________.
Answer: (506)
Exp: The graph formed by the description contains 4 vertices of degree 3 and 40verices of degree 5
and 100 vertices of degree 8.
According to sum of the degrees theorem 4*3+40*5+100*8 = 2|E| |E| = 1012/2 = 506
52. An ordered n-tuple (d1,d2,...,dn) with 1 2 n d d .... d ≥ ≥ ≥ is called graphic if there exists a
simple undirected graph with n vertices having degrees 1 2 n d ,d ,...,d respectively. Which of
the following 6-tuples is NOT graphic?
(A) (1, 1, 1, 1, 1, 1) (B) (2, 2, 2, 2, 2, 2)
(C) (3, 3, 3, 1, 0, 0) (D) (3, 2, 1, 1, 1, 0)
Answer: (C)
Exp: According to havel-hakimi theorem
(1,1,1,1,1,1) is graphic iff<1,1,1,1,0> is graphic
(0,1,1,1,1) is graphic iff (0,1,1,0) is graphic
(0,0,1,1) is graphic iff (0,0,0) is graphic
Since (0,0,0) is graphic (1,1,1,1,1,1) is also graphic.
(The process is always finding maximum degree and removing it from degree sequence,
subtract 1 from each degree for d times from right to left where d is maximum degree)
(2,2,2,2,2,2) is graphic iff (2,2,22-1,2-1) = (2,2,2,1,1) is graphic.
(1,1,2,2,2) is graphic iff (1,1,1,1) is graphic.
(1,1,1,1) is graphic iff (0,1,1)
(0,1,1) is graphic iff (0,0) is graphic.
Since (0,0) is graphic (2,2,2,2,2,2) is also graphic.
Consider option C now.
(3,3,3,1,0,0)(0,0,1,3,3,3) is graphic iff (0,0,0,2,2) is graphic.
Note that before applying the havel-hakimi step degree sequence should be in non-increasing
order.
(0,0,0,2,2) is graphic iff (0,0,-1,1) is graphic.
Since (0,0,-1,1) is not graphic (3,3,3,1,0,0) is also not graphic.
53. Which one of the following propositional logic formulas is TRUE when exactly two of p, q,
and r are TRUE?
(A) ((p q r V p q ~ r ↔ ∧ ∧ ∧ ) ) ( ) (B) (~ p q r V p q ~ r ( ↔ ∧ ∧ ∧ ) ) ( ) (C) ((p q r V p q ~ r → ∧ ∧ ∧ ) ) ( ) (D) (~ p q r p q ~ r ( ↔ ∧ ∧ ∧ ∧ ) ) ( ) India’s No.1 institute for GATE Training 1 Lakh+ Students trained till date 65+ Centers across India 31
Answer: (B)
Exp: P = T q=F and r=T
Option A will become false.
Option C will become false.
Option D is always false.
54. Given the following schema:
employees(emp-id, first-name, last-name, hire-date,
dept-id, salary)
departments(dept-id, dept-name, manager-id, location-id)
You want to display the last names and hire dates of all latest hires in their respective
departments in the location ID 1700. You issue the following query:
SQL>SELECT last-name, hire-date
FROM employees
WHERE (dept-id, hire-date) IN
(SELECT dept-id, MAX(hire-date)
FROM employees JOIN departments USING(dept-id)
WHERE location-id = 1700
GROUP BY dept-id);
What is the outcome?
(A) It executes but does not give the correct result.
(B) It executes and gives the correct result.
(C) It generates an error because of pairwise comparison.
(D) It generates an error because the GROUP BY clause cannot be used with table joins in a sub-query.
Answer: (B)
Exp: In the inner sub query, “employees” and “departments” tables are joined by “using” clause
(first Cartesian product of those two tables will be done and then and wherever these is a match on the dept-ids that tuple will be filtered). After this, the tuples of the resultant table will be filtered by using the condition “location-id=1700” and then will grouped on dept-id(all the tuples having equal values under dept-id will come into one group). After grouping,the columns dept-id in location-id 1700 and maximum of hire dates in that respective dept-id will be selected. Format of the tuples in the resultant table will be dept-id in location-id 1700 along with the latest hire date in the respective dept (two columns). Outer query takes each tuple from “employees” table and it will check whether dept-id and hire-date pair for this tuple is contained in the table given by inner sub query. If this is the case it will display the last-name of respective employee IN operator compares one or multiple expressions on the left side of the operator to a set of one or more values on the right side of the operator. When using multiple expressions (like 2
columns - pair wise comparison), the number and data types of expressions in the list must match on both sides of the operator.
55. Consider two processors P1 and P2 executing the same instruction set. Assume that under
identical conditions, for the same input, a program running on P2 takes 25% less time but
incurs 20% more CPI (clock cycles per instruction) as compared to the program running on
P1. If the clock frequency of P1 is 1GHz, then the clock frequency of P2 (in GHz) is
_________.
Answer: (1.6)
Exp: 1 cycle time for
9
1
10 p 1n.s
1GH= =Assume 1
p takes 5 cycles for a program then 2
p takes 20% more, means, 6 cycles.
2
p Takes 25% less time, means, if 1
p takes 5 n.s, then 2
p takes 3.75 n.s.
Assume 2
p clock frequency is x GHz.
2
p Taken 6 cycles, so
9
6 10 3.75, x 1.6
x GH
sentence below?
It is fascinating to see life forms cope with varied environmental conditions.
(A) Adopt to (B) Adapt to (C) Adept in (D) Accept with
Answer: (B)
2. Choose the most appropriate word from the options given below to complete the following
sentence.
He could not understand the judges awarding her the first prize, because he thought that her
performance was quite ___________________.
(A) Superb (B) Medium (C) Mediocre (D) Exhilarating
Answer: (C)
3. In a press meet on the recent scam, the minister said, “The buck stops here”. What did the
minister convey by the statement?
(A) He wants all the money (B) He will return the money
(C) He will assume final responsibility (D) He will resist all enquiries
Answer: (C)
4. If ( ) ( )
2 2 2 z 1/ z 98, compute z 1/ z + = +
Answer: (96)
Exp: Expanding
2 2
2 2
1 1 1 z 2.z. 98 z 96
z z z
+ + = ⇒ + =
5. The roots of 2
ax bx c 0 + + = are real and positive a, b and c are real. Then 2
ax b x c 0 + + =
has
(A) No roots (B) 2 real roots (C) 3 real roots (D) 4 real roots
Answer: (D)
Exp: ax2
+bx+c=0
for roots to be real & +ve
b2
-4ac>0
This will have 2 real positive roots.
2
ax b x c 0 + + =
This can be written as;
2
2
ax bx c
Discri min ant b 4ac 0
+ +
= − >
2
2
2
ax bx c
( b) 4ac
b 4ac
− +
− −
⇒ −
Is also >0. This will have real roots
⇒ This will have 4 real roots.
CS-GATE-2014 PAPER-01| www.gateforum.com
India’s No.1 institute for GATE Training 1 Lakh+ Students trained till date 65+ Centers across India
2
Q.No. 6 – 10 Carry One Mark Each
6. The Palghat Gap (or Palakkad Gap), a region about 30 km wide in the southern part of the
Western Ghats in India, is lower than the hilly terrain to its north and south. The exact
reasons for the formation of this gap are not clear. It results in the neighbouring regions of
Tamil Nadu getting more rainfall from the South West monsoon and the neighbouring
regions of Kerala having higher summer temperatures.
What can be inferred from this passage?
(A) The Palghat gap is caused by high rainfall and high temperatures in southern Tamil Nadu
and Kerala
(B) The regions in Tamil Nadu and Kerala that are near the Palghat Gap are low–lying
(C) The low terrain of the Palghat Gap has a significant impact on weather patterns in
neighbouring parts of Tamil Nadu and Kerala
(D) Higher summer temperatures result in higher rainfall near the Palghat Gap area
Answer: (C)
7. Geneticists say that they are very close to confirming the genetic roots of psychiatric illnesses
such as depression and schizophrenia, and consequently, that doctors will be able to eradicate
these diseases through early identification and gene therapy.
On which of the following assumptions does the statement above rely?
(A) Strategies are now available for eliminating psychiatric illnesses
(B) Certain psychiatric illnesses have a genetic basis
(C) All human diseases can be traced back to genes and how they are expressed
(D) In the future, genetics will become the only relevant field for identifying psychiatric
illnesses
Answer: (B)
8. Round–trip tickets to a tourist destination are eligible for a discount of 10% on the total fare.
In addition, groups of 4 or more get a discount of 5% on the total fare. If the one way single
person fare is Rs 100, a group of 5 tourists purchasing round–trip tickets will be charged Rs
___________
Answer: (850)
Exp: One way force =100
Two way fare per person=200
5 persons=1000/-
Total discount applicable=10+5=15%
15 Discount amount 1000 150
100
= × =
Amount to be paid=1000-150=850
9. In a survey, 300 respondents were asked whether they own a vehicle or not. If yes, they were
further asked to mention whether they own a car or scooter or both. Their responses are
tabulated below. What percent of respondents do not own a scooter?
Men Women
Own vehicle
Car 40 34
Scooter 30 20
Both 60 46
Do not own vehicle 20 50
Answer: (48)
Exp: Total respondents=300
Those who don’t have scooter
⇒ Men= 40+20=60
84 Women 34 50
144
144 % 100 48%
300
= + =
= × =
10. When a point inside of a tetrahedron (a solid with four triangular surfaces) is connected by
straight lines to its corners, how many (new) internal planes are created with these lines?
_______________________
Answer: (6)
4
Q. No. 1 – 25 Carry One Mark Each
1. Consider the statement:
“Not all that glitters is gold”
Predicate glitters (x) is true if x glitters and predicate gold (x) is true if x is gold. Which one
of the following logical formulae represents the above statement?
(A) ∀x; glitters x gold x ( ) ⇒¬ ( ) (B) ∀x; gold x glitters x ( ) ⇒ ( )
(C) ∃ ∧ ¬ x; gold x glitters x ( ) ( ) (D) ∃ ∧ ¬ x; glitters x gold x ( ) ( )
Answer: (D)
Exp: It means “It is false that every glitter is gold” or “some glitters are not gold”.
Then we can say “atleast one glitter object is not gold”.
2. Suppose you break a stick of unit length at a point chosen uniformly at random. Then the
expected length of the shorter stick is ________ .
Answer: (0.25)
Exp: The smaller sticks, therefore, will range in length from almost 0 meters up to a maximum of
0.5 meters, with each length equally possible.
Thus, the average length will be about 0.25 meters, or about a quarter of the stick.
3. Let G=(V,E) be a directed graph where V is the set of vertices and E the set of edges. Then
which one of the following graphs has the same strongly connected components as G?
(A G V,E where E u,v | u,v E ) 1 1 1 = = ∉ ( ) {( ) ( ) }
(B G V,E where E u,v | v,u E ) 2 2 2 = = ∉ ( ) {( ) ( ) }
(C G V,E where E u,v | there is a path of length 2 from ) 3 3 3 = = ≤ ( ) {( ) u to v in E}
(D G V ,E where V is the set of vertices in G which are ) 4 4 4 = ( ) not isolated
Answer: (B)
Exp: Take an example for Graph G
. .
A B
Then option A and D will be eliminated.
Let G is below graph
Then G3 is a graph with below structure
In G the numbers of strongly connected components are 2 where as in G3 it is only one.
A B
A B
4 Consider the following system of equations:
3x 2y 1
4x 7z 1
x y z 3
x 2y 7z 0
+ =
+ =
+ + =
− + =
The number of solutions for this system is __________________
Answer: (1)
Exp: 3x 2y 1
4x 7z 1
x y z 3
x 2y 7z 0
+ =
+ =
+ + =
− + =
Augmented matrix is
3 2 0 1
4 0 7 1
1 1 1 3
1 2 7 0
−
1 3
1 1 1 3
4 0 7 1
R R
3 2 0 1
1 2 7 0
↔
−
2 2 1 3 3 1 4 4 1
3 3 2
4 4 2
4 4 3
R R 4R R R 3R , R R R
1 1 1 3
0 4 3 11
0 1 3 8
0 3 6 3
1 1 1 3
R 4R R
0 4 3 11
0 0 15 21
R 4R 3R
0 0 15 21
1 1 1 3
0 4 3 11
R R R
0 0 15 21
0 0 0 0
→ − → − → −
− −
− − − − −
→ −
− −
− −
→ −
− −
→ +
− −
(A : B A 3 no. of variables ) ( )
Unique solution exists
ρ = ρ = =
∴
5. The value of the dot product of the eigenvectors corresponding to any pair of different eigen
values of a 4-by-4 symmetric positive definite matrix is ______________.
Answer: (0)
Exp: ( The eigen vectors corresponding to distinct eigen values of real symmetric matrix are
orthogonal)
6. Let the function
( ) ( ) ( ) ( )
( ) ( ) ( )
sin cos tan
f sin cos tan 6 6 6
sin cos tan 3 3 3
θ θ θ
θ = π π π
π π π
Where ,
6 2
π π θ =∈ and f '(θ) denote the derivative of f with respect to θ . Which of the
following statement is / are TRUE?
(I) There exists ,
6 3
π π θ∈ such that f ' 0 (θ =) .
(II) There exists ,
6 3
π π θ∈ such that f ' 0 (θ ≠) .
(A) I only (B) II only (C) Both I and II (D) Neither I nor II
Answer: (C)
Exp: (By Mean value theorem)
7. Consider the following Boolean expression for F:
F P,Q,R,S PQ PQR PQRS ( ) = + +
The minimal sum-of products form of F is
(A PQ QR QS ) + + (B P Q R S ) + + +
(C P Q R S ) + + + (D PR PRS P ) + +
Answer: (A)
Exp: PQ PQR PQRS + +
( )
( ) ( )( ) ( )( )
( )
( ) ( )
PQ PQ R RS
PQ PQ R R R S A BC A B A C
PQ PQ R S R R 1
Q P P R S
= + +
= + + + + = + +
= + + + =
= + +
∵
∵
(( )( )) ( )( )
( )
Q P P P R S A BC A B A C
Q P R S P P 1
PQ QR QS
= + + + + = + +
= + + + =
= + +
∵
∵
8. The base (or radix) of the number system such that the following equation holds
is____________.
312 13.1
20
=
Answer: (5)
Exp: Let ‘x’ be the base or radix of the number system
( )
o 2
o 1
o
2
2 2
2 2
2
2 x 1 x 3 x 3 x 1 x 1 x
0 x 2 x
2 x 3x 1 3 x
2x x
3x x 2 3x x 1
2x x
3x x 2 6x 2x 2
x 5x 0
x x 5 0
x 0 or x 5
× + × + × −
= × + × + ×
× + ×
+ +
⇒ = + +
+ + + +
⇒ =
⇒ + + = + +
⇒ − =
⇒ − =
⇒ = =
As base or radix of a number system cannot be zero, here x 5 =
9. A machine has a 32-bit architecture, with 1-word long instructions. It has 64 registers, each of
which is 32 bits long. It needs to support 45 instructions, which have an immediate operand
in addition to two register operands. Assuming that the immediate operand is an unsigned
integer, the maximum value of the immediate operand is ____________.
Answer: (16383)
Exp: 1 Word 32 bits =
Each instruction has 32 bits
To support 45 instructions, opcode must contain 6-bits
Register operand1 requires 6 bits, since the total registers are 64.
Register operand 2 also requires 6 bits
14-bits are left over for immediate Operand Using 14-bits, we can give maximum 16383,
Since ( )
14 2 16384 from 0 to 16383 =
6 6 6 14
32 bits
opcode Re g opd 1 Re g opd 2
immediate
opnd
10. Consider the following program in C language:
( )
( )
( )
# include stdio.h
main
{
int i;
int * pi &i;
scanf "%d", pi ;
pr int f "%d \ n", i 5 ;
}
< >
=
+
Which one of the following statements is TRUE?
(A) Compilation fails.
(B) Execution results in a run-time error.
(C) On execution, the value printed is 5 more than the address of variable i.
(D) On execution, the value printed is 5 more than the integer value entered.
Answer: (D)
Exp: pi contains the address of i. So scanf("%d",pi) places the value entered in console into
variable i.e So printf("%d\n",i+5),prints 5 more than the value entered in console.
11. Let G be a graph with n vertices and m edges. What is the tightest upper bound on the
running time of Depth First Search on G, when G is represented as an adjacency matrix?
(A) θ(n) (B) θ + (n m) (C) ( )
2
θ n (D) ( )
2
θ m
Answer: (C)
Exp: DFS visits each vertex once and as it visits each vertex, we need to find all of its neighbours
to figure out where to search next. Finding all its neighbours in an adjacency matrix requires
O(V ) time, so overall the running time will be O(V2
).
12. Consider rooted n node binary tree represented using pointers. The best upper bound on the
time required to determine the number of sub trees having exactly 4 nodes is ( )
a b 0 n log n .
Then the value of a + 10b is_______
Answer: 1
Exp: int print_subtrees_size_4(node *n)
{
int size=0;
if(node==null)
return 0;
size=print_subtrees_size_4(node->left)+print_subtrees_size_4(node->right)+1;
if(size==4)
printf("this is a subtree of size 4");
return size;
}
The above function on taking input the root of a binary tree prints all the subtrees of size 4 in
O(n) time
so a=1 , b=0 and then a+10b=1
13. Consider the directed graph given below.
Which one of the following is TRUE?
(A) The graph does not have any topological ordering
(B) Both PQRS and SRQP are topological orderings
(C) Both PSRQ and SPRQ are topological orderings.
(D) PSRQ is the only topological ordering.
Answer: (C)
Exp: Topological ordering of a directed graph is a linear ordering of its vertices such that for every
directed edge uv from vertex u to vertex v, u comes before v in the ordering. Topological
ordering is possible iff graph has no directed cycles.
(A) As the given graph doesn’t contain any directed cycles, it has at least one topological
ordering. So option (A) is false
(B) PQRS cannot be topological ordering because S should come before R in the ordering as
there is a directed edge from S to R.
SRQP cannot be topological ordering, because P should come before Q in the ordering as
there is a directed edge from P to Q
(C) PSRQ and SPRQ are topological orderings as both of then satisfy the above mentioned
topological ordering conditions.
(D) PSRQ is not the only one topological ordering as SPRQ is other possibility
14. Let P be a quick sort program to sort numbers in ascending order using the first element as
the pivot. Let t1 and t2 and t2 be the number of comparisons made by P for the inputs [1 2 3 4
5] and [4 1 5 3 2] respectively. Which one of the following holds?
(A) t1 =5 (B) t1 < t2 (C) t1>t2 (D) t1 = t2
Answer: (C)
Exp: Partition algorithm for quick sort
( ) [ ]
[ ] [ ]
[ ]
[ ] [ ]
[ ] [ ]
Partition A,P,q // A P,.....q
x A P // pivot A P
i P
for j P 1 to q
do if A j x
then i i 1
exchange A i A j
exchangeA P A i
← =
←
= +
≤
← +
↔
↔
return i [returning where pivot element is there after partitioning]
Recursively call the above algorithm for the two sub arrays [elements before and after pivot
element] to complete the sorting.
P Q
R S
x pivot
1 2 3 4 5
i j
=
2 1 ? NO ≤
Pivot x A B[ ]
1 2 3 4 5
i j
= =
3 2 ? NO ≤
1 2 3 4 5
i j 3 1 ? NO ≤
1 2 3 4 5
i j 4 2 ? NO ≤
1 2 3 4 5
i j 4 1 ? NO ≤
1 2 3 4 5
i j 5 2 ? NO ≤
1 2 3 4 5
i j 5 1 ? NO ≤
exchange A P & A J [ ] [ ]
exchange A P & A i [ ] [ ]
x Pivot A P[ ]
1 2 3 4 5
i j
= =
4 3 ? NO ≤
x Pivot
1 2 3 4 5
i j
=
5 4 ? NO ≤
1 2 3 4 5
i j 5 3 ? NO ≤
exchange A P & A i [ ] [ ]
exchange A P & A i [ ] [ ]
1 2 3 4 5 ∴ Total 10 conparisons
Pivot ≥Pivot
1 2 3 4 5
Pivot ≥Pivot
1 2 3 4 5
Pivot ≥Pivot
Call recursively
for this
1 2 3 4 5
Pivot ≥ Pivot Call recursively
for this subarray
[ ]
[ ] [ ]
[ ] [ ]
x pivot A P
4 1 5 3 2
i j 1 4?Yes
i i 1 exchange A i & A j & increment j
4 1 5 3 2
i j 5 4?NO
4 1 5 3 2
i j 3 4?Yes
i i 1 exchange A i & A j & increment j
4 1 3 5 2
i J 2 4?Yes
= =
≤
← +
≤
≤
← +
≤
[ ] [ ]
i i 1
4 1 3 2 5
i j
exchange A P & A i
← + ( )
[ ] [ ]
x pivot A P
2 1 3 | 4 | 5
i j 1 2 ? yes
2 1 3 | 4 | 5
i j 3 2 ? NO
exchange A P & A i
= =
≤
≤
∴6 conparisons
15. Which one of the following is TRUE?
(A) The language L = { }
n n a b | n 0 ≥ is regular.
(B) The language L = { }
n
a | n is prime is regular.
(C) The language L = { w | w has 3k 1b's + for some k ∈ N with Σ = {a,b} } is regular.
(D) The language L = { { }}
* ww | w with 0,1 ∈Σ Σ = is regular.
Answer: (C)
Exp: (A) { }
n n L a b n 0 = ≥ is a CFL but not regular, it requires memory for the representation
(B) { }
n L a n is prime = is neither regular nor CFL
(C) L w | w has 3K 1 b's for some k N with = + ∈ { }
Σ = {a,b}
is a regular language, since the total count of b’s are multiple of 3 plus one. The regular
expression is a * ba * a *ba *ba * ba * * a * ba * ba * ba * *a * ba * ( ) +( )
(D) L ww | w * with 0,1 = ∈Σ Σ = { { }} is neither regular nor CFL
1 2 3 4 5
Pivot
2 1 3 4 5
≤Pivot Pivot ≥Pivot
16. Consider the finite automaton in the following figure.
What is the set of reachable states for the input string 0011?
(A) {q ,q ,q 0 1 2 } (B) {q ,q 0 1} (C) {q ,q ,q ,q 0 1 2 3} (D) {q3}
Answer: (A)
Exp: δ = δ (q ,0011 q ,011 0 0 ) ( )
( )
( ) { }
( ) ( )
{ } { }
{ }
0
0 1
0 1
0 1 2
0 1 2
q ,11
q ,q ,1
q ,1 q ,1
q ,q q
q ,q ,q
= δ
= δ
= δ ∪ δ
= ∪
=
17. Which one of the following is FALSE?
(A) A basic block is a sequence of instructions where control enters the sequence at the
beginning and exits at the end.
(B) Available expression analysis can be used for common subexpression elimination.
(C) Live variable analysis can be used for dead code elimination
(D) x 4*5 x 20 = ⇒ = is an example of common subexpression elimination
Answer: (D)
Exp: x 4 5 x 20 = × ⇒ = is not an example of common sub-expression but it is constant folding. In
constant folding expression consisting of constants will be replaced by their final value at
compile time, rather than doing the calculation in run-time.
18. Match the following
(1) Waterfall model (a) Specifications can be developed
(2) Evolutionary model (b) Requirements compromises are inevitable
(3) Component based software (c) Explicit recognition of risk
(4) Spiral development (d) Inflexible partitioning of the project into stages
(A) 1-a, 2-b, 3-c, 4-d (B) 1-d, 2-a, 3-b, 4-c
(C) 1-d, 2-b, 3-a, 4-c (D) 1-c, 2-a, 3-b, 4-d
Answer: (B)
Exp: The main drawback of the waterfall model is the difficulty of accommodating change after
the process is underway. One phase has to be complete before moving onto the next phase.
Inflexible partitioning of the project into distinct stages in waterfall model makes it difficult
to respond to changing customer requirements.
Evolutionary software models are iterative. They are characterized in manner that enables the
software engineers to develop increasingly more complete version of software.
In Spiral model, Development can be divided in to smaller parts and more risky parts can be
developed earlier which helps better risk management.
0,1
0
q 1
q 2
q 3
q
1 0,1 0,1
1
19. Suppose a disk has 201 cylinders, numbered from 0 to 200. At some time the disk arm is at
cylinder 100, and there is a queue of disk access requests for cylinders 30, 85, 90, 100, 105,
110, 135 and 145. If Shortest-Seek Time First (SSTF) is being used for scheduling the disk
access, the request for cylinder 90 is serviced after servicing ____________ number of
requests.
Answer: (3)
Exp:
Request for cylinder is served after serving 3 requests (100,105 and 110)
20. Which one of the following is FALSE?
(A) User level threads are not scheduled by the kernel.
(B) When a user level thread is blocked, all other threads of its process are blocked.
(C) Context switching between user level threads is faster than context switching between
kernel level threads.
(D) Kernel level threads cannot share the code segment.
Answer: (D)
Exp: User threads are supported above the kernel and a managed without kernel support. The
thread function library to implement user level threads usually runs on top of the system in
user mode. Thus these threads with in a process are invisible to the operating system. Since
the kernel is unaware of the existence of such threads; when one user level thread is blocked
in the kernel all other threads of its process are blocked. So options (A) and (B) are true
(C) The OS is aware of kernel level threads. Kernel threads are scheduled by the OS’s
scheduling algorithms and require a “lightweight” context switch to switch between
(that is, registers, PC and SP must be changed, but the memory context remains the same
among kernel threads in the (same process). User level threads are much faster to switch
between as there is not context switch
(D) False
Kernel level threads within the same process share code section, data section and other
operating system resources such as open files and signals.
100
105
110
90
85
135
145
30
21. Consider the relation scheme R = (E, F, G, H, I, J, K, L, M, N) and the set of functional
dependencies {{E,F}→ {G},{F}→ {I,J , E,H K,L M } { } → → { } ( ) , {K M , } →{ } }
{L N } →{ } on R. What is the key for R?
(A) {E, F} (B) {E, F, H} (C) {E, F, H, K, L} (D) {E}
Answer: (B)
Exp: R EFGHI,JKLMN ( )
F {
EF G
F IJ
EH KL
K M
L
}
=
→
→
→
→
→ Ν
( ) EF EFGIJ, E & F +
= Together functionally derive GIJ and if we observe given FDs, H
can’t be determined by any other attributes. So H must be part of all the (candidate) keys. H
along with E determines K and L, K & L functionally determine M and N respectively.
( ) EFH EFGIJHKLMN + ∴ =
∴ EFH is the only candidate for key.
22. Given the following statements:
S1: A foreign key declaration can always be replaced by an equivalent check
assertion in SQL
S2: Given the table R(a,b,c) where a and b together form the primary key, the following is a
valid table definition.
CREATE TABLE S (
a INTEGER,
d INTEGER,
e INTEGER,
PRIMARY KEY (d),
FOREIGN KEY (a) references R)
Which one of the following statements is CORRECT?
(A) S1 is TRUE and S2 is a FALSE (B) Both S1 and S2 are TRUE
(C) S1 is FALSE and S2 is a TRUE (D) Both S1 and S2 are FALSE
Answer: (D)
Exp: S1: Manager (Name, DeptID)
Department (DeptName, Deptid)
In given relation Manager DeptID is a foreign key referencing Deptid (P.K) of relation
Department.
Let’s declare the foreign key by an equivalent check assertion as follows:-
CREATE TABLE Manager (
Name Varchar (10)
DeptID INT (6) check (DeptID IN ( select Deptid from Department)),
PRIMARY KEY (Name)
);
The above use of check assertion is good to declare the foreign key as far as insertion is
considered for relation manager (will not insert any tuple in Manager containing such DeptID
value which is not present in any tuple of Department).
But the above declaration will fail to implement changes done in Department relation in
terms of deletion & updation. For an instance if a deptid present in Department gets deleted,
then respective reference in Manager should also be deleted.
∴ S1 is false.
S2: The given table definition is not valid due to invalid foreign key declaration. Attribute a
is declared as foreign key which is a single valued attribute and it is referencing the primary
key (ab) of relation R (a, b, c), which is a composite key.
A single value attribute cannot refer a composite key.
4 S2 is false.
23. Consider the following three statements about link state and distance vector routing protocols,
for a large network with 500 network nodes and 4000 links
[S1] The computational overhead in link state protocols is higher than in distance vector
protocols.
[S2] A distance vector protocol (with split horizon) avoids persistent routing loops, but not
a link state protocol.
[S3] After a topology change, a link state protocol will converge faster than a distance
vector protocol.
Which one of the following is correct about S1, S2, and S3?
(A) S1, S2, and S3 are all true (B) S1, S2, and S3 are all false.
(C) S1 and S2 are true, but S3 is false (D) S1 and S3 are true, but S2 is false.
Answer: (D)
Exp: Statement S1
The Distance Vector routing protocols rely on the information from their directly connected
neighbours in order to calculate and accumulate route information. Distance Vector routing
protocols require very little overhead as compared to Link State routing protocols as
measured by memory and processor power while the Link State routing protocols do not rely
solely on the information from the neighbours or adjacent router in order to calculate route
information. Instead, Link State routing protocols have a system of databases that they use in
order to calculate the best route to destinations in the network. This is TRUE
Statement S3
Distance Vector exchanges the routing updates periodically whether the topology is change
or not, this will maximize the convergence time which increases the chance of routing loops
while the Link State routing protocols send triggered change based updates when there is a
topology change. After initial flood, pass small event based triggered link state updates to all
other routers. This will minimize the convergence time that’s why there is no chance of
routing loops. This is TRUE.
24. Which one of the following are used to generate a message digest by the network security
protocols?
(P) RSA (Q) SHA-1 (R) DES (S) MD5
(A) P and R only (B) Q and R only (C) Q and S only (D) R and S only
Answer: (C)
Exp: RSA and DES are for Encryption where MD5 and SHA – 1 are used to generate Message
Digest.
25. Identify the correct order in which the following actions take place in an interaction between
a web browser and a web server.
1. The web browser requests a webpage using HTTP.
2. The web browser establishes a TCP connection with the web server.
3. The web server sends the requested webpage using HTTP.
4. The web browser resolves the domain name using DNS.
(A) 4,2,1,3 (B) 1,2,3,4 (C) 4,1,2,3 (D) 2,4,1,3
Answer: (A)
Exp: First of all the browser must now know what IP to connect to. For this purpose browser takes
help of Domain name system (DNS) servers which are used for resolving hostnames to IP
addresses. As browser is an HTTP client and as HTTP is based on the TCP/IP protocols, first
it establishes a TCP connection with the web server and requests a webpage using HTTP, and
then the web server sends the requested webpage using HTTP. Hence the order is 4,2,1,3
Q.No. 26 – 55 Carry Two Marks
26. Consider a token ring network with a length of 2km having 10 stations including a
monitoring station. The propagation speed of the signal is 2 x 108
m/s and the token
transmission time is ignored. If each station is allowed to hold the token for 2 μsec, the
minimum time for which the monitoring station should wait (in μsec) before assuming that
the token is lost is _______.
Answer: (28μs to 30μs)
Exp: Given Length (d) = 2 Km
No. of Stations (m) = 10
Propagation Speed (v) = 2 × 108
m/s
THT = 2μs
So, Max. TRT = TP in the Ring + No. of Active Stations * THT
= 10 × 10-6 + 10 × 2 × 10-6
= 30 μs
27. Let the size of congestion window of a TCP connection be 32 KB when a timeout occurs.
The round trip time of the connection is 100 msec and the maximum segment size used is
2kB. The time taken (in msec) by the TCP connection to get back to 32KB congestion
window is ______
Answer: (1100 to 1300)
Exp: Given that at the time of Time Out, Congestion Window Size is 32KB and RTT = 100ms
When Time Out occurs, for the next round of Slow Start, Threshold = (size of Cwnd) / 2
It means Threshold = 16KB
Slow Start
2KB
1RTT
4KB
2RTT
8KB
3RTT
16KB ----------- Threshold reaches. So Additive Increase Starts
4RTT
18KB
5RTT
20KB
6RTT
22KB
7RTT
24KB
8RTT
26KB
9RTT
28KB
10RTT
30KB
11RTT
32KB
So, Total no. of RTTs = 11 → 11 * 100 = 1100
28. Consider a selective repeat sliding window protocol that uses a frame size of 1 KB to send
data on a 1.5 Mbps link with a one-way latency of 50 msec. To achieve a link utilization of
60%, the minimum number of bits required to represent the sequence number field is
________.
Answer: (5)
Exp:
p
Given L 1KB
B 1.5Mbps
T 50ms
60%
=
=
=
η =
Efficiency formula for SR protocol is
p
x
W 60 W T
a
1 2a 100 1 2a T
η = ⇒ = =
+ +
∵
3
x 6
L 8 10 T 5.3ms
B 1.5 10
×
= = =
×
p
x
T 50 500 a 9.43
T 5.3 53
= = = =
60 W W 11.9 12
100 19.86
⇒ = ⇒ = ≈
⇒ W 2 12 2 24 2 24 2 n 5 n 1 n n 5 −
= = ⇒ = ⇒ = ≈ ⇒ =
29. Consider the following four schedules due to three transactions (indicted by the subscript)
using read and write on a data item x, denoted r (x) and w (x) respectively. Which one of
them is conflict serializable?
(A) r1 (x) ; r2 (x) ; w1 (x) ; r3(x) ; w2 (x) (B) r2 (x) ; r1 (x) ; w2 (x) ; r3(x) ; w1 (x)
(C) r3 (x) ; r2 (x) ; r1 (x) ; w2(x) ; w1 (x) (D) r2 (x) ; w2 (x) ; r3 (x) ; r1(x) ; w1 (x)
Answer: (D)
Exp: If there is a cycle in precedence graph, then the schedule is not conflict serializable.
(A) (B)
Not conflict serializable not conflict serializable
(C) (D)
Not conflict serializable it is conflict equivalent to
2 3 1
3 2 1
T T T &
T T T
→ →
→ →
T1 T2
T3
T1 T2
T3
T2
T3
T1
T1 T2
T3
T1 T2
T3
30. Given the following two statements:
S1: Every table with two single-valued attributes is in 1NF, 2NF, 3NF and BCNF
S2 : AB C, D E, E C → → → is a minimal cover for the set of functional
dependencies AB C, D E, AB E,E C → → → →
Which one of the following is CORRECT?
(A) S1 is TRUE and S2 is FALSE. (B) Both S1 and S2 are TRUE.
(C) S1 is FALSE and S2 is TRUE. (D) Both S1 and S2 are FALSE.
Answer: (A)
Exp: S : True 1
Consider any table R with two attributes R A.B ( )
The possible FD sets are
F { 1
A B
}
Key : A and is in BCNF
=
→
F { 2
B A
}
Key : B and is in BCNF
=
→
F { 3
A B
B A
}
Key : A & B It is in BCNF
=
→
→
F { 4
}
Key : AB and is in BCNF
=
If a table is in BCNF it is also in 1NF, 2NF and 3NF also
S : False 2
First FD set cannot cover second FD set because in second FD set AB can functionally derive
E but that is not happing in first FD set.
31. An operating system uses the Banker’s algorithm for deadlock avoidance when managing the
allocation of three resource types X, Y, and Z to three processes P0, P1, and P2. The table
given below presents the current system state. Here, the Allocation matrix shows the current
number of resources of each type allocated to each process and the Max matrix shows the
maximum number of resources of each type required by each process during its execution.
There are 3 units of type X, 2 units of type Y and 2 units of type Z still available. The system
is currently in a safe state. Consider the following independent requests for additional
resources in the current state:
REQ1: P0 requests 0 units of X, 0 units of Y and 2 units of Z
REQ2: P1 requests 2 units of X, 0 units of Y and 0 units of Z
Allocation Max
X Y Z
0 0 1
3 2 0
2 1 1
X Y Z
8 4 3
6 2 0
3 3 3
P0
P1
P2
Which one of the following is TRUE?
(A) Only REQ1 can be permitted.
(B) Only REQ2 can be permitted.
(C) Both REQ1 and REQ2 can be permitted.
(D) Neither REQ1 nor REQ2 can be permitted.
Answer: (B)
Exp: REQ1
Once P0
is allocated with (0,0,2) , the status of the system will be as follows
Allocation Max Need Available
X Y Z
0 0 3
3 2 0
2 1 1
X Y Z
8 4 3
6 2 0
3 3 3
X Y Z
8 4 0
3 0 0
1 2 2
X Y Z
3 2 0
With available ( ) 1
3,2,0 only P can be served. Once P1
is executed, available will be (6,4,0) ,
with (6,4,0) we can’t serve either P or P 0 2 . Hence there is no safe sequence. Hence REQ1
can’t be permitted.
REQ2
Once P1
is allocated with (2,0,0) , the status of the system will be as follows
Allocated Max Need Available
0
1
2
P
P
P
X Y Z
0 0 1
5 2 0
2 1 1
X Y Z
8 4 3
6 2 0
3 3 3
X Y Z
8 4 2
1 0 0
1 2 2
X Y Z
1 2 2
With available (1,2,2), we can serve either P or P 1 2 .
If we serve P1
then the safe sequence is P ,P ,P 1 2 0 . If we serve P2
then the safe sequence is
P ,P ,P 2 1 0 . As true is at least one safe sequence we can permit REQ2.
32. Consider the following set of processes that need to be scheduled on a single CPU. All the
times are given in milliseconds
Process Name Arrival Time Execution Time
A 0 6
B 3 2
C 5 4
D 7 6
E 10 3
Using the shortest remaining time first scheduling algorithm, the average process turnaround
time (in msec) is ____________________.
Answer: (7.2)
Exp:
A B A C E D
0 3 5 8 12 15 21
(8 0 5 3 12 5 21 7 15 10 ) ( ) ( ) ( ) ( )
Average turn around time
5
36 7.2ms
5
− + − + − + − + −
=
= ⇒
33. Assume that there are 3 page frames which are initially empty. If the page reference string 1,
2, 3, 4, 2, 1, 5, 3, 2, 4, 6, the number of page faults using the optimal replacement policy is
___________
Answer: (7)
Exp:
1 2 3 4 2 1 5 3 2 4
3 4 4 4 4 4 4 4 4
2 2 2 2 2 2 2 2 2 6
1 1 1 1 1 1 5 3 3 3 3
F F F F H H F F H H F
7 page faults
34. A canonical set of items is given below
s L. R
Q R.
→ >
→
On input symbol < the set has
(A) a shift-reduce conflict and a reduce-reduce conflict.
(B) a shift-reduce conflict but not a reduce-reduce conflict.
(C) a reduce-reduce conflict but not a shift-reduce conflict.
(D) neither a shift-reduce nor a reduce-reduce conflict.
Answer: (D)
Exp:
>
From above diagram, we can see that there is no shift- reduce or reduce-reduce conflict.
→ >
→
S L . R
Q R.
S L . R → >
old I
new I
35. Let L be a language and L be its complement. Which of the following is NOT a viable
possibility?
(A) Neither L nor L is recursively enumerable (r.e.).
(B) One of L and L is r.e. but not recursive; the other is not r.e.
(C) Both L and L are r.e. but not recursive.
(D) Both L and L are recursive.
Answer: (C)
Exp: Recursive languages are closed under complement.
If a language L is recursive enumerable but not recursive then its complement is not a
recursive enumerable, so both L and L are recursive enumerable but not recursive is not a
viable possibility.
36. Which of the regular expressions given below represent the following DFA?
I) 0*1(1+00*1)*
II) 0*1*1+11*0*1
III) (0+1)*1
(A) I and II only (B) I and III only
(C) II and III only (D) I, II, and III
Answer: (B)
Exp: Given DFA will accept all the strings over ε ={0,1} which are ending with 1.
0*1 1 00*1 * and 0 1 *1, ( + + ) ( ) are the regular expressions for ending with 1.
37. There are 5 bags labelled 1 to 5. All the coins in a given bag have the same weight. Some
bags have coins of weight 10 gm, others have coins of weight 11 gm. I pick 1, 2, 4, 8, 16
coins respectively from bags 1 to 5. Their total weight comes out to 323 gm. Then the product
of the labels of the bags having 11 gm coins is ___.
Answer: 12
Exp: Let the weight of coins in the respective bags (1 through 5) be a,b,c,d and e-each of which
can take one of two values namely 10 or 11 (gm).
Now, the given information on total weight can be expressed as the following equation:
1.a+2.b+4.c+8.d+16.e = 323
⇒ a must be odd ⇒ a = 11
The equation then becomes:
11+2.b+4.c+8.d+16.e = 323
0 0 1
1
⇒ 2.b+4.c+8.d+16.e = 312
⇒ b+2.c+4.d+8.e = 156
⇒ b must be even ⇒ b = 10
The equation then becomes:
10+2.c+4.d+8.e = 156
⇒ 2.c+4.d+8.e = 146
⇒ c+2.d+4.e = 73
⇒ c must be odd ⇒ c = 11
The equation now becomes:
11+2.d+4.e = 73
⇒ 2.d+4.e = 62
⇒ d+2.e = 31
⇒ e = 11 and e = 10
Therefore, bags labelled 1, 3 and 4 contain 11 gm coins ⇒ Required Product = 1*3*4* = 12.
38. Suppose a polynomial time algorithm is discovered that correctly computes the largest clique
in a given graph. In this scenario, which one of the following represents the correct Venn
diagram of the complexity classes P, NP and NP Complete (NPC)?
Answer: (D)
Exp: The most important open question in complexity theory is whether the P = NP , which asks
whether polynomial time algorithms actually exist for NP-complete and all NP problems (
since a problem “C” is in NP-complete, iff C is in NP and every problem in NP is reducible
to C in polynomial time). In the given question it is given that some polynomial time
algorithm exists which computes the largest clique problem in the given graph which is
known NP-complete problem. Hence P=NP=NP-Complete.
(A)
P
NPC
NP
(B)
P NP
NPC
(B)
NPC P NP =
(D)
P NP NPC = =
CS-GATE-2014 PAPER-01| www.gateforum.com
India’s No.1 institute for GATE Training 1 Lakh+ Students trained till date 65+ Centers across India
24
39. The minimum number of comparisons required to find the minimum and the maximum of
100 numbers is _________________.
Answer: (148)
Exp: From the list of given n numbers [say n is even],
Pick up first two elements, compare them
assign Current min min of two numbers
Current max max of two numbers
− =
− =
From the remaining n 2 − numbers, take pairs wise and follow this process given below.
1. Compare two elements
Assign min = min of two numbers
max = max of two numbers
2. Compare min and current - min
Assign current min min current min,min − = − { }
3. Compare max and current - max
Assign current max max current max,max − = − { }
Repeat above procedure for all the remaining pairs of numbers. We can observe that each of
pair requires 3 comparisons
1. for finding min and max
2. For updating current – min
3. for updating current – max
But for initial pair we need only one comparison not 3.
3 n 2 ( ) 3n 3n total number of comparisons 1 3 1 2
2 2 2
−
∴ = + = − + = −
Here n 100, = so number of comparisons = 148.
40. Consider a hash table with 9 slots. The hash function is h k k mod 9. ( ) = The collisions are
resolved by chaining. The following 9 keys are inserted in the order: 5, 28, 19, 15, 20, 33, 12,
17, 10. The maximum, minimum, and average chain lengths in the hash table, respectively,
are
(A) 3, 0, and 1 (B) 3, 3, and 3 (C) 4, 0, and 1 (D) 3, 0, and 2
Answer: (A)
Exp:
Maximum & minimum chain lengths are 3 & 0 respectively
0 3 1 1 0 1 2 0 1 Average chain length 1
9
∴
+ + + + + + + +
= =
41. Consider the following C function in which size is the number of elements in the array E:
int MyX(int *E, unsigned int size)
{
int Y = 0;
int Z;
int i, j, k;
for(i = 0; i < size; i++)
Y = Y + E[i];
for(i = 0; i < size; i++)
for(j = i; j < size; j++)
{
Z = 0;
for(k = i; k <= j; k++)
Z = Z + E[k];
if (Z > Y)
Y = Z;
}
return Y;
}
The value returned by the function MyX is the
(A) maximum possible sum of elements in any sub-array of array E.
(B) maximum element in any sub-array of array E.
(C) sum of the maximum elements in all possible sub-arrays of array E.
(D) the sum of all the elements in the array E.
Answer: (A)
0
1
2
3
4
5
6
7
8
28 19 10
20
12
5
15 33
17
Exp: int Myx int * E, unsin ged int sixe ( )
( )
[ ]
( )
( )
( )
[ ]
{
int Y 0;
int z;
int i, j,k;
for i 0;i size;i Calculates sum of the elements
Y Y E i of the array E and stores it in Y
for i 0; i size; i
for j i; j size; j
{ calculates the sum of elements o
z 0;
for k i;k j; k
z z E k ;
=
= < + +
= +
= < + +
= < + +
=
= <= + +
= +
( )
f
all posible subarrays of E
if z Y Checks whether sum of elements of each subarray
Y z; is greaer than the sum of elements of array if so,that sum
} is assigned to Y, if not 'Y' will be the sum of elements of
return Y; complete array
}
> →
=Ultimately returns the maximum possible sum of elements in any sub array of given array E.
42. Consider the following pseudo code. What is the total number of multiplications to be
performed?
D= 2
for i = 1 to n do
for j = i to n do
for k = j + 1 to n do
D = D * 3
(A) Half of the product of the 3 consecutive integers
(B) One-third of the product of the 3 consecutive integers.
(C) One-sixth of the product of the 3 consecutive integers.
(D) None of the above.
Answer: (C)
Exp:
( )
i 1, j 1, k 2 to n n 1 times
i 1, j 2, k 3 to n n 2 times
i 1, j 3, k 4 to n n 3 times
n 1 times
:
i 1, j n 2, k n 1 to n 2 times
i 1, j n 1, k n to n 1 time
= = = ⇒ −
= = = ⇒ −
= = = ⇒ −
∑ −
= = − = − ⇒
= = − = ⇒
( )
i 2, j 2,k 3 to n n 2 times
i 2, j 3,k 4 to n n 3 times
: : n 2 times
: :
i 2, j n 1,k n to n 1 time
:
:
i n 1, j n 1,k n to n 1 time } 1 times
= = = ⇒ −
= = = ⇒ −
∑ −
= = − = ⇒
= − = − = ⇒ ∑
( )
( ) ( ) ( )
( )
( )( ) ( ) ( )( )( )
1
2 3 n 1
S
S S S
n 1
i
i 1
2
Total number of multiplications
1 2 3 ...... n 1
1 1 2 1 2 3 .... 1 2 3 ..n 1
n n 1
S
2
1 1
n n
2 2
1 1 n n 1 2n 1 n n 1 n 1 n n 1
2 6 2 2 6
−
↓
↓ ↓ ↓
−
=
∴
⇒ ∑ + ∑ + ∑ + ∑ −
= + + + + + + + + + + −
−
= = ∑
= ∑ − ∑
+ + + − +
= − =
∑
43. Consider a 6-stage instruction pipeline, where all stages are perfectly balanced. Assume that there is no cycle-time overhead of pipelining. When an application is executing on this 6-stage pipeline, the speedup achieved with respect to non-pipelined execution if 25% of the instructions incur 2 pipeline stall cycles is ______________________.
Answer: (4)
Exp: For 6 stages, non- pipelining takes 6 cycles.
There were 2 stall cycles for pipelining for 25% of the instructions
25 So pipe line time 1 2
100
3
1.5
2
Non pipeline time 6 Speed up 4
Pipeline time 1.5
= +
= =
−
= = =
44. An access sequence of cache block addresses is of length N and contains n unique block
addresses. The number of unique block addresses between two consecutive accesses to the
same block address is bounded above K. What is the miss ratio if the access sequence is
passed through a cache of associativity A k ≥ exercising least-recently-used replacement
policy?
(A) n/N (B) l/N (C) 1/A (D) k/n
Answer: (A)
45. Consider the 4-to-1 multiplexer with two lines S1 and S0 given below.
The minimal sum of-products form of the Boolean expression for the output F of the
multiplexer is
(A) PQ QR PQR + + (B) PQ PQR PQR PQR + + +
(C) PQR PQR QR PQR + + + (D) PQR
Answer: (A)
Exp: PQ.O PQ.1 PQ.R PQR + + +
= + + PQ PQ.R PQR
Hence the minimized expression is PQ QR PQR + +
46. The function f(x) = x sin x satisfies the following equation. f"(x) + f(x) +tcosx = 0. The value
of t is______.
Answer: -2
Exp: Given f " x f x t cos x 0 ( ) + + = ( )
and f (x) xsin x
f ' x x cos x sin x
f " x x sin x cos x cos x
2cos x xsin x
2cos x f x
2cos x f x f x t cos x 0
2cos x t cos x t 2
=
= +
= − + +
= −
= −
∴ − + + =
⇒ =− ⇒ = −
0
1
R
R
0
1
2
3
1
s 0
s
4 to 1
Multiplexer
− −
F
P Q
PQ QR QR QR QR
P 1
P
1
1 1
QR
PQR
47. A function f(x) is continuous the interval [0,2]. It is known that f(0) = f(2) = -1 and f(1) = 1.
Which one of the following statements must be true?
(A) There exists a y in the interval (0,1) such that f(y) = f(y + 1)
(B) For every y in the interval (0,1), f(y) = f(2 - y)
(C) The maximum value of the function in the interval (0.2) is 1
(D) There exists a y in the interval (0,1) such that f(y) =f(2 – y)
Answer: (A)
Exp: Define g(x) =f(x)-f(x+1) in [0,1]. g(0) is negative and g(1) is positive. By intermediate value
theorem there is y€(0,1) such that g(y)=0
That is f(y) =f(y+1).
Thus answer is (a)
48. For fair six-sided dice are rolled. The probability that the sum of the results being 22is
X
1296. The value of X is _________
Answer: (10)
Exp: 22 occurred in following ways
6 6 6 4 4ways
6 6 5 5 6ways
→
→
Required probability = 6 4 10 x 10
2296 2296
+
= ⇒ =
49. A pennant is a sequence of numbers, each number being 1 or 2. An n-pennant is a sequence
of numbers with sum equal to n. For example, (1,1,2) is a 4-pennant. The set of all possible 1-
pennants is {(1)}, the set of all possible 2-pennants is {(2), (1,1)}and the set of all 3-pennants
is {(2,1), (1,1,1), (1,2)}. Note that the pennant (1,2) is not the same as the pennant (2,1). The
number of 10- pennants is ______________.
Answer: (89)
Exp: No twos: 1111111111⇒1 pennant
Single two: 211111111⇒9!/8!1! = 9 pennants
Two twos: 22111111⇒8!/6!.2! = 28
Three twos: 2221111⇒7!/3!.4! = 35
Four twos: 222211⇒6!/4!.2! = 15
Five twos: 22222⇒1
Total = 89 pennants.
50. Let S denote the set of all functions { } { } 4
f : 0,1 0,1 → . Denote by N the number of functions
from S to the set {0,1}. The value of log2 log2 N is______.
Answer: (16)
Exp: The number of functions from A to B where size of A = |A| and size of B = |B| is |B||A|
{0,1}4
= {0,1}X{0,1}X{0,1}X{0,1} = 16
|S| = 216
N = 2|S|
loglog N = log log 2|S| = log |S| = log 216 = 16
51. Consider an undirected graph G where self-loops are not allowed. The vertex set of G is {i,
f): 1 ≤ i ≤ 12, 1 ≤ j ≤ 12}. There is an edge between (a,b) and (c,d) if a c 1 − ≤ and
b d 1 − ≤ The number of edges in the graph is _____________.
Answer: (506)
Exp: The graph formed by the description contains 4 vertices of degree 3 and 40verices of degree 5
and 100 vertices of degree 8.
According to sum of the degrees theorem 4*3+40*5+100*8 = 2|E| |E| = 1012/2 = 506
52. An ordered n-tuple (d1,d2,...,dn) with 1 2 n d d .... d ≥ ≥ ≥ is called graphic if there exists a
simple undirected graph with n vertices having degrees 1 2 n d ,d ,...,d respectively. Which of
the following 6-tuples is NOT graphic?
(A) (1, 1, 1, 1, 1, 1) (B) (2, 2, 2, 2, 2, 2)
(C) (3, 3, 3, 1, 0, 0) (D) (3, 2, 1, 1, 1, 0)
Answer: (C)
Exp: According to havel-hakimi theorem
(1,1,1,1,1,1) is graphic iff<1,1,1,1,0> is graphic
(0,1,1,1,1) is graphic iff (0,1,1,0) is graphic
(0,0,1,1) is graphic iff (0,0,0) is graphic
Since (0,0,0) is graphic (1,1,1,1,1,1) is also graphic.
(The process is always finding maximum degree and removing it from degree sequence,
subtract 1 from each degree for d times from right to left where d is maximum degree)
(2,2,2,2,2,2) is graphic iff (2,2,22-1,2-1) = (2,2,2,1,1) is graphic.
(1,1,2,2,2) is graphic iff (1,1,1,1) is graphic.
(1,1,1,1) is graphic iff (0,1,1)
(0,1,1) is graphic iff (0,0) is graphic.
Since (0,0) is graphic (2,2,2,2,2,2) is also graphic.
Consider option C now.
(3,3,3,1,0,0)(0,0,1,3,3,3) is graphic iff (0,0,0,2,2) is graphic.
Note that before applying the havel-hakimi step degree sequence should be in non-increasing
order.
(0,0,0,2,2) is graphic iff (0,0,-1,1) is graphic.
Since (0,0,-1,1) is not graphic (3,3,3,1,0,0) is also not graphic.
53. Which one of the following propositional logic formulas is TRUE when exactly two of p, q,
and r are TRUE?
(A) ((p q r V p q ~ r ↔ ∧ ∧ ∧ ) ) ( ) (B) (~ p q r V p q ~ r ( ↔ ∧ ∧ ∧ ) ) ( ) (C) ((p q r V p q ~ r → ∧ ∧ ∧ ) ) ( ) (D) (~ p q r p q ~ r ( ↔ ∧ ∧ ∧ ∧ ) ) ( ) India’s No.1 institute for GATE Training 1 Lakh+ Students trained till date 65+ Centers across India 31
Answer: (B)
Exp: P = T q=F and r=T
Option A will become false.
Option C will become false.
Option D is always false.
54. Given the following schema:
employees(emp-id, first-name, last-name, hire-date,
dept-id, salary)
departments(dept-id, dept-name, manager-id, location-id)
You want to display the last names and hire dates of all latest hires in their respective
departments in the location ID 1700. You issue the following query:
SQL>SELECT last-name, hire-date
FROM employees
WHERE (dept-id, hire-date) IN
(SELECT dept-id, MAX(hire-date)
FROM employees JOIN departments USING(dept-id)
WHERE location-id = 1700
GROUP BY dept-id);
What is the outcome?
(A) It executes but does not give the correct result.
(B) It executes and gives the correct result.
(C) It generates an error because of pairwise comparison.
(D) It generates an error because the GROUP BY clause cannot be used with table joins in a sub-query.
Answer: (B)
Exp: In the inner sub query, “employees” and “departments” tables are joined by “using” clause
(first Cartesian product of those two tables will be done and then and wherever these is a match on the dept-ids that tuple will be filtered). After this, the tuples of the resultant table will be filtered by using the condition “location-id=1700” and then will grouped on dept-id(all the tuples having equal values under dept-id will come into one group). After grouping,the columns dept-id in location-id 1700 and maximum of hire dates in that respective dept-id will be selected. Format of the tuples in the resultant table will be dept-id in location-id 1700 along with the latest hire date in the respective dept (two columns). Outer query takes each tuple from “employees” table and it will check whether dept-id and hire-date pair for this tuple is contained in the table given by inner sub query. If this is the case it will display the last-name of respective employee IN operator compares one or multiple expressions on the left side of the operator to a set of one or more values on the right side of the operator. When using multiple expressions (like 2
columns - pair wise comparison), the number and data types of expressions in the list must match on both sides of the operator.
55. Consider two processors P1 and P2 executing the same instruction set. Assume that under
identical conditions, for the same input, a program running on P2 takes 25% less time but
incurs 20% more CPI (clock cycles per instruction) as compared to the program running on
P1. If the clock frequency of P1 is 1GHz, then the clock frequency of P2 (in GHz) is
_________.
Answer: (1.6)
Exp: 1 cycle time for
9
1
10 p 1n.s
1GH= =Assume 1
p takes 5 cycles for a program then 2
p takes 20% more, means, 6 cycles.
2
p Takes 25% less time, means, if 1
p takes 5 n.s, then 2
p takes 3.75 n.s.
Assume 2
p clock frequency is x GHz.
2
p Taken 6 cycles, so
9
6 10 3.75, x 1.6
x GH








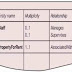
No comments