GATE (CS/IT) Question and Answer Set-2 2016
Q. 1 – Q. 5 carry one mark each.
Q.1 The man who is now Municipal Commissioner worked as ____________________.
(A) the security guard at a university
(B) a security guard at the university
(C) a security guard at university
(D) the security guard at the university
Answer :- (B)
Q.2 Nobody knows how the Indian cricket team is going to cope with the difficult and seamer-friendly
wickets in Australia.
Choose the option which is closest in meaning to the underlined phrase in the above sentence.
(A) put up with (B) put in with (C) put down to (D) put up against
Answer :- (A)
Q.3 Find the odd one in the following group of words.
mock, deride, praise, jeer
(A) mock (B) deride (C) praise (D) jeer
Answer :- (C)
Q.4 Pick the odd one from the following options.
(A) CADBE (B) JHKIL (C) XVYWZ (D) ONPMQ
Answer :- (D)
Q.5 In a quadratic function, the value of the product of the roots (α, β) is 4. Find the value of αn + βn/α−n + β−n
(A) n4 (B) 4n (C) 22n-1 (D) 4n-1
Answer :- (B)
Q. 6 – Q. 10 carry two marks each.
Q.6 Among 150 faculty members in an institute, 55 are connected with each other through Facebook®
and 85 are connected through WhatsApp®. 30 faculty members do not have Facebook® or
WhatsApp® accounts. The number of faculty members connected only through Facebook® accounts
is ______________.
(A) 35 (B) 45 (C) 65 (D) 90
Answer :- (D)
Q.7 Computers were invented for performing only high-end useful computations. However, it is no
understatement that they have taken over our world today. The internet, for example, is ubiquitous.
Many believe that the internet itself is an unintended consequence of the original invention. With
the advent of mobile computing on our phones, a whole new dimension is now enabled. One is left
wondering if all these developments are good or, more importantly, required.
Which of the statement(s) below is/are logically valid and can be inferred from the above
paragraph?
(i) The author believes that computers are not good for us.
(ii) Mobile computers and the internet are both intended inventions
(A) (i) only (B) (ii) only (C) both (i) and (ii) (D) neither (i) nor (ii)
Answer :- (D)
Q.8 All hill-stations have a lake. Ooty has two lakes.
Which of the statement(s) below is/are logically valid and can be inferred from the above
sentences?
(i) Ooty is not a hill-station.
(ii) No hill-station can have more than one lake.
(A) (i) only (B) (ii) only
(C) both (i) and (ii) (D) neither (i) nor (ii)
Answer :- (D)
Q.9 In a 2 × 4 rectangle grid shown below, each cell is a rectangle. How many rectangles can be
observed in the grid?
(A) 21 (B) 27 (C) 30 (D) 36
Answer :- (C)
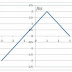
Q.10 Choose the correct expression for f(x) given in the graph.
(A) ff(xx) = 1 − |xx − 1| (B) ff(xx) = 1 + |xx − 1|
(C) ff(xx) = 2 − |xx − 1| (D) ff(xx) = 2 + |xx − 1|
Answer :- (C)
Q. 1 - Q. 25 carry one mark each.
Q.1 Consider the following expressions:
(i) false
(ii) Q
(iii) true
(iv) P∨Q
(v) ¬Q∨P
The number of expressions given above that are logically implied by P ∧ (P ⇒ Q) is______________.
Answer :- 4.0 : 4.0
Q.2 Let f(x) be a polynomial and g(x) = f0
(x) be its derivative. If the degree of (f(x)+ f(−x)) is10, then the degree of (g(x)−g(−x)) is_____________ .
Answer :- 9.0 : 9.0
Q.3 The minimum number of colours that is sufficient to vertex-colour any planar graph is_____________.
Answer :- 4.0 : 4.0
Q.4 Consider the systems, each consisting of m linear equations in n variables.
I. If m < n, then all such systems have a solution
II. If m > n, then none of these systems has a solution
III. If m = n, then there exists a system which has a solution
Which one of the following is CORRECT?
(A) I, II and III are true
(B) Only II and III are true
(C) Only III is true
(D) None of them is true
Answer :- (C)
Q.5 Suppose that a shop has an equal number of LED bulbs of two different types. The probability
of an LED bulb lasting more than 100 hours given that it is of Type 1 is 0.7, and given that it
is of Type 2 is 0.4. The probability that an LED bulb chosen uniformly at random lasts more
than 100 hours is .
Answer :- 0.55 : 0.55
Q.6 Suppose that the eigenvalues of matrix A are 1,2,4. The determinant of (A−1)T is__________.
Answer :-0.124 : 0.126
Q.7 Consider an eight-bit ripple-carry adder for computing the sum of A and B, where A and B are integers represented in 2’s complement form. If the decimal value of A is one, the decimal
value of B that leads to the longest latency for the sum to stabilize is ___________.
Answer :- -1.0 : 1.0
Q.8 Let, x1⊕x2⊕x3⊕x4 = 0 where x1, x2, x3, x4 are Boolean variables, and ⊕ is the XOR operator.
Which one of the following must always be TRUE?
(A) x1x2x3x4 = 0
(B) x1x3 +x2 = 0
(C) x ̄1 ⊕x ̄3 = x ̄2 ⊕x ̄4
(D) x1 +x2 +x3 +x4 = 0
Answer :- (C)
Q.9 Let X be the number of distinct 16-bit integers in 2’s complement representation. Let Y be the
number of distinct 16-bit integers in sign magnitude representation.
Then X −Y is ___________.
Answer :- 1.0 : 1.0
Q.10 A processor has 40 distinct instructions and 24 general purpose registers. A 32-bit instruction
word has an opcode, two register operands and an immediate operand. The number of bits
available for the immediate operand field is _________.
Answer :- 16.0 : 16.0
Q.11 Breadth First Search (BFS) is started on a binary tree beginning from the root vertex. There is a vertex t at a distance four from the root. If t is the n-th vertex in this BFS traversal, then the
maximum possible value of n is ___________ .
Answer :- 31.0 : 31.0
Q.12 The value printed by the following program is _______.
void f(int* p, int m){
m = m + 5;
*p = *p + m;
return;
}
void main(){
int i=5, j=10;
f(&i, j);
printf("%d", i+j);
}
Answer :- 30.0 : 30.0
Q.13 Assume that the algorithms considered here sort the input sequences in ascending order. If the
input is already in ascending order, which of the following are TRUE?
I. Quicksort runs in Θ(n2) time
II. Bubblesort runs in Θ(n2) time
III. Mergesort runs in Θ(n) time
IV. Insertion sort runs in Θ(n) time
(A) I and II only
(B) I and III only
(C) II and IV only
(D) I and IV only
Answer :- (D)
Q.14 The Floyd-Warshall algorithm for all-pair shortest paths computation is based on
(A) Greedy paradigm.
(B) Divide-and-Conquer paradigm.
(C) Dynamic Programming paradigm.
(D) neither Greedy nor Divide-and-Conquer nor Dynamic Programming paradigm.
Answer :- (C)
Q.15 N items are stored in a sorted doubly linked list. For a delete operation, a pointer is provided
to the record to be deleted. For a decrease-key operation, a pointer is provided to the record on
which the operation is to be performed.
An algorithm performs the following operations on the list in this order: Θ(N) delete, O(logN)
insert, O(logN) find, and Θ(N) decrease-key. What is the time complexity of all these
operations put together?
(A) O(log2N) (B) O(N) (C) O(N2) (D) Θ(N2logN)
Answer :- (C)
Q.16 The number of states in the minimum sized DFA that accepts the language defined by the
regular expression (0+1)∗(0+1)(0+1)∗is ________.
Answer :- 2.0 : 2.0
Q.17 Language L1 is defined by the grammar: S1 → aS1b|ε
Language L2 is defined by the grammar: S2 → abS2|ε
Consider the following statements:
P: L1 is regular
Q: L2 is regular
Which one of the following is TRUE?
(A) Both P and Q are true
(B) P is true and Q is false
(C) P is false and Q is true
(D) Both P and Q are false
Answer :- (C)
Q.18 Consider the following types of languages: L1 : Regular, L2 : Context-free, L3 : Recursive,
L4 : Recursively enumerable. Which of the following is/are TRUE?
I. L3 ∪L4 is recursively enumerable
II. L2 ∪L3 is recursive
III. L∗1 ∩L2 is context-free
IV. L1 ∪L2 is context-free
(A) I only
(B) I and III only
(C) I and IV only
(D) I, II and III only
Answer :- (D)
Q.19 Match the following:
(P) Lexical analysis (i) Leftmost derivation
(Q) Top down parsing (ii) Type checking
(R) Semantic analysis (iii) Regular expressions
(S) Runtime environments (iv) Activation records
(A) P ↔ i, Q ↔ ii, R ↔ iv, S ↔ iii
(B) P ↔ iii, Q ↔ i, R ↔ ii, S ↔ iv
(C) P ↔ ii, Q ↔ iii, R ↔ i, S ↔ iv
(D) P ↔ iv, Q ↔ i, R ↔ ii, S ↔ iii
Answer :- (B)
Q.20 In which one of the following page replacement algorithms it is possible for the page fault rate
to increase even when the number of allocated frames increases?
(A) LRU (Least Recently Used)
(B) OPT (Optimal Page Replacement)
(C) MRU (Most Recently Used)
(D) FIFO (First In First Out)
Answer :- (D)
Q.21 B+ Trees are considered BALANCED because
(A) the lengths of the paths from the root to all leaf nodes are all equal.
(B) the lengths of the paths from the root to all leaf nodes differ from each other by at
most 1.
(C) the number of children of any two non-leaf sibling nodes differ by at most 1.
(D) the number of records in any two leaf nodes differ by at most 1.
Answer :- (A)
Q.22 Suppose a database schedule S involves transactions T1, ..., Tn. Construct the precedence
graph of S with vertices representing the transactions and edges representing the conflicts. If
S is serializable, which one of the following orderings of the vertices of the precedence graph
is guaranteed to yield a serial schedule?
(A) Topological order
(B) Depth-first order
(C) Breadth-first order
(D) Ascending order of transaction indices
Answer :- (A)
Q.23 Anarkali digitally signs a message and sends it to Salim. Verification of the signature by Salim
requires
(A) Anarkali’s public key.
(B) Salim’s public key.
(C) Salim’s private key.
(D) Anarkali’s private key.
Answer :- (A)
Q.24 In an Ethernet local area network, which one of the following statements is TRUE?
(A) A station stops to sense the channel once it starts transmitting a frame.
(B) The purpose of the jamming signal is to pad the frames that are smaller than the minimum frame size.
(C) A station continues to transmit the packet even after the collision is detected.
(D) The exponential backoff mechanism reduces the probability of collision on retransmissions.
Answer :- (D)
Q.25 Identify the correct sequence in which the following packets are transmitted on the network
by a host when a browser requests a webpage from a remote server, assuming that the host has
just been restarted.
(A) HTTP GET request, DNS query, TCP SYN
(B) DNS query, HTTP GET request, TCP SYN
(C) DNS query, TCP SYN, HTTP GET request
(D) TCP SYN, DNS query, HTTP GET request
Answer :- (C)
Q.1 The man who is now Municipal Commissioner worked as ____________________.
(A) the security guard at a university
(B) a security guard at the university
(C) a security guard at university
(D) the security guard at the university
Answer :- (B)
Q.2 Nobody knows how the Indian cricket team is going to cope with the difficult and seamer-friendly
wickets in Australia.
Choose the option which is closest in meaning to the underlined phrase in the above sentence.
(A) put up with (B) put in with (C) put down to (D) put up against
Answer :- (A)
Q.3 Find the odd one in the following group of words.
mock, deride, praise, jeer
(A) mock (B) deride (C) praise (D) jeer
Answer :- (C)
Q.4 Pick the odd one from the following options.
(A) CADBE (B) JHKIL (C) XVYWZ (D) ONPMQ
Answer :- (D)
Q.5 In a quadratic function, the value of the product of the roots (α, β) is 4. Find the value of αn + βn/α−n + β−n
(A) n4 (B) 4n (C) 22n-1 (D) 4n-1
Answer :- (B)
Q. 6 – Q. 10 carry two marks each.
Q.6 Among 150 faculty members in an institute, 55 are connected with each other through Facebook®
and 85 are connected through WhatsApp®. 30 faculty members do not have Facebook® or
WhatsApp® accounts. The number of faculty members connected only through Facebook® accounts
is ______________.
(A) 35 (B) 45 (C) 65 (D) 90
Answer :- (D)
Q.7 Computers were invented for performing only high-end useful computations. However, it is no
understatement that they have taken over our world today. The internet, for example, is ubiquitous.
Many believe that the internet itself is an unintended consequence of the original invention. With
the advent of mobile computing on our phones, a whole new dimension is now enabled. One is left
wondering if all these developments are good or, more importantly, required.
Which of the statement(s) below is/are logically valid and can be inferred from the above
paragraph?
(i) The author believes that computers are not good for us.
(ii) Mobile computers and the internet are both intended inventions
(A) (i) only (B) (ii) only (C) both (i) and (ii) (D) neither (i) nor (ii)
Answer :- (D)
Q.8 All hill-stations have a lake. Ooty has two lakes.
Which of the statement(s) below is/are logically valid and can be inferred from the above
sentences?
(i) Ooty is not a hill-station.
(ii) No hill-station can have more than one lake.
(A) (i) only (B) (ii) only
(C) both (i) and (ii) (D) neither (i) nor (ii)
Answer :- (D)
Q.9 In a 2 × 4 rectangle grid shown below, each cell is a rectangle. How many rectangles can be
observed in the grid?
(A) 21 (B) 27 (C) 30 (D) 36
Answer :- (C)
Q.10 Choose the correct expression for f(x) given in the graph.
(A) ff(xx) = 1 − |xx − 1| (B) ff(xx) = 1 + |xx − 1|
(C) ff(xx) = 2 − |xx − 1| (D) ff(xx) = 2 + |xx − 1|
Answer :- (C)
Q. 1 - Q. 25 carry one mark each.
Q.1 Consider the following expressions:
(i) false
(ii) Q
(iii) true
(iv) P∨Q
(v) ¬Q∨P
The number of expressions given above that are logically implied by P ∧ (P ⇒ Q) is______________.
Answer :- 4.0 : 4.0
Q.2 Let f(x) be a polynomial and g(x) = f0
(x) be its derivative. If the degree of (f(x)+ f(−x)) is10, then the degree of (g(x)−g(−x)) is_____________ .
Answer :- 9.0 : 9.0
Q.3 The minimum number of colours that is sufficient to vertex-colour any planar graph is_____________.
Answer :- 4.0 : 4.0
Q.4 Consider the systems, each consisting of m linear equations in n variables.
I. If m < n, then all such systems have a solution
II. If m > n, then none of these systems has a solution
III. If m = n, then there exists a system which has a solution
Which one of the following is CORRECT?
(A) I, II and III are true
(B) Only II and III are true
(C) Only III is true
(D) None of them is true
Answer :- (C)
Q.5 Suppose that a shop has an equal number of LED bulbs of two different types. The probability
of an LED bulb lasting more than 100 hours given that it is of Type 1 is 0.7, and given that it
is of Type 2 is 0.4. The probability that an LED bulb chosen uniformly at random lasts more
than 100 hours is .
Answer :- 0.55 : 0.55
Q.6 Suppose that the eigenvalues of matrix A are 1,2,4. The determinant of (A−1)T is__________.
Answer :-0.124 : 0.126
Q.7 Consider an eight-bit ripple-carry adder for computing the sum of A and B, where A and B are integers represented in 2’s complement form. If the decimal value of A is one, the decimal
value of B that leads to the longest latency for the sum to stabilize is ___________.
Answer :- -1.0 : 1.0
Q.8 Let, x1⊕x2⊕x3⊕x4 = 0 where x1, x2, x3, x4 are Boolean variables, and ⊕ is the XOR operator.
Which one of the following must always be TRUE?
(A) x1x2x3x4 = 0
(B) x1x3 +x2 = 0
(C) x ̄1 ⊕x ̄3 = x ̄2 ⊕x ̄4
(D) x1 +x2 +x3 +x4 = 0
Answer :- (C)
Q.9 Let X be the number of distinct 16-bit integers in 2’s complement representation. Let Y be the
number of distinct 16-bit integers in sign magnitude representation.
Then X −Y is ___________.
Answer :- 1.0 : 1.0
Q.10 A processor has 40 distinct instructions and 24 general purpose registers. A 32-bit instruction
word has an opcode, two register operands and an immediate operand. The number of bits
available for the immediate operand field is _________.
Answer :- 16.0 : 16.0
Q.11 Breadth First Search (BFS) is started on a binary tree beginning from the root vertex. There is a vertex t at a distance four from the root. If t is the n-th vertex in this BFS traversal, then the
maximum possible value of n is ___________ .
Answer :- 31.0 : 31.0
Q.12 The value printed by the following program is _______.
void f(int* p, int m){
m = m + 5;
*p = *p + m;
return;
}
void main(){
int i=5, j=10;
f(&i, j);
printf("%d", i+j);
}
Answer :- 30.0 : 30.0
Q.13 Assume that the algorithms considered here sort the input sequences in ascending order. If the
input is already in ascending order, which of the following are TRUE?
I. Quicksort runs in Θ(n2) time
II. Bubblesort runs in Θ(n2) time
III. Mergesort runs in Θ(n) time
IV. Insertion sort runs in Θ(n) time
(A) I and II only
(B) I and III only
(C) II and IV only
(D) I and IV only
Answer :- (D)
Q.14 The Floyd-Warshall algorithm for all-pair shortest paths computation is based on
(A) Greedy paradigm.
(B) Divide-and-Conquer paradigm.
(C) Dynamic Programming paradigm.
(D) neither Greedy nor Divide-and-Conquer nor Dynamic Programming paradigm.
Answer :- (C)
Q.15 N items are stored in a sorted doubly linked list. For a delete operation, a pointer is provided
to the record to be deleted. For a decrease-key operation, a pointer is provided to the record on
which the operation is to be performed.
An algorithm performs the following operations on the list in this order: Θ(N) delete, O(logN)
insert, O(logN) find, and Θ(N) decrease-key. What is the time complexity of all these
operations put together?
(A) O(log2N) (B) O(N) (C) O(N2) (D) Θ(N2logN)
Answer :- (C)
Q.16 The number of states in the minimum sized DFA that accepts the language defined by the
regular expression (0+1)∗(0+1)(0+1)∗is ________.
Answer :- 2.0 : 2.0
Q.17 Language L1 is defined by the grammar: S1 → aS1b|ε
Language L2 is defined by the grammar: S2 → abS2|ε
Consider the following statements:
P: L1 is regular
Q: L2 is regular
Which one of the following is TRUE?
(A) Both P and Q are true
(B) P is true and Q is false
(C) P is false and Q is true
(D) Both P and Q are false
Answer :- (C)
Q.18 Consider the following types of languages: L1 : Regular, L2 : Context-free, L3 : Recursive,
L4 : Recursively enumerable. Which of the following is/are TRUE?
I. L3 ∪L4 is recursively enumerable
II. L2 ∪L3 is recursive
III. L∗1 ∩L2 is context-free
IV. L1 ∪L2 is context-free
(A) I only
(B) I and III only
(C) I and IV only
(D) I, II and III only
Answer :- (D)
Q.19 Match the following:
(P) Lexical analysis (i) Leftmost derivation
(Q) Top down parsing (ii) Type checking
(R) Semantic analysis (iii) Regular expressions
(S) Runtime environments (iv) Activation records
(A) P ↔ i, Q ↔ ii, R ↔ iv, S ↔ iii
(B) P ↔ iii, Q ↔ i, R ↔ ii, S ↔ iv
(C) P ↔ ii, Q ↔ iii, R ↔ i, S ↔ iv
(D) P ↔ iv, Q ↔ i, R ↔ ii, S ↔ iii
Answer :- (B)
Q.20 In which one of the following page replacement algorithms it is possible for the page fault rate
to increase even when the number of allocated frames increases?
(A) LRU (Least Recently Used)
(B) OPT (Optimal Page Replacement)
(C) MRU (Most Recently Used)
(D) FIFO (First In First Out)
Answer :- (D)
Q.21 B+ Trees are considered BALANCED because
(A) the lengths of the paths from the root to all leaf nodes are all equal.
(B) the lengths of the paths from the root to all leaf nodes differ from each other by at
most 1.
(C) the number of children of any two non-leaf sibling nodes differ by at most 1.
(D) the number of records in any two leaf nodes differ by at most 1.
Answer :- (A)
Q.22 Suppose a database schedule S involves transactions T1, ..., Tn. Construct the precedence
graph of S with vertices representing the transactions and edges representing the conflicts. If
S is serializable, which one of the following orderings of the vertices of the precedence graph
is guaranteed to yield a serial schedule?
(A) Topological order
(B) Depth-first order
(C) Breadth-first order
(D) Ascending order of transaction indices
Answer :- (A)
Q.23 Anarkali digitally signs a message and sends it to Salim. Verification of the signature by Salim
requires
(A) Anarkali’s public key.
(B) Salim’s public key.
(C) Salim’s private key.
(D) Anarkali’s private key.
Answer :- (A)
Q.24 In an Ethernet local area network, which one of the following statements is TRUE?
(A) A station stops to sense the channel once it starts transmitting a frame.
(B) The purpose of the jamming signal is to pad the frames that are smaller than the minimum frame size.
(C) A station continues to transmit the packet even after the collision is detected.
(D) The exponential backoff mechanism reduces the probability of collision on retransmissions.
Answer :- (D)
Q.25 Identify the correct sequence in which the following packets are transmitted on the network
by a host when a browser requests a webpage from a remote server, assuming that the host has
just been restarted.
(A) HTTP GET request, DNS query, TCP SYN
(B) DNS query, HTTP GET request, TCP SYN
(C) DNS query, TCP SYN, HTTP GET request
(D) TCP SYN, DNS query, HTTP GET request
Answer :- (C)









No comments